[ad_1]

Important Addons for Elementor, a well-liked WordPress plugin utilized in over 1,000,000 websites, has been discovered to have a important distant code execution (RCE) vulnerability in model 5.0.4 and older.
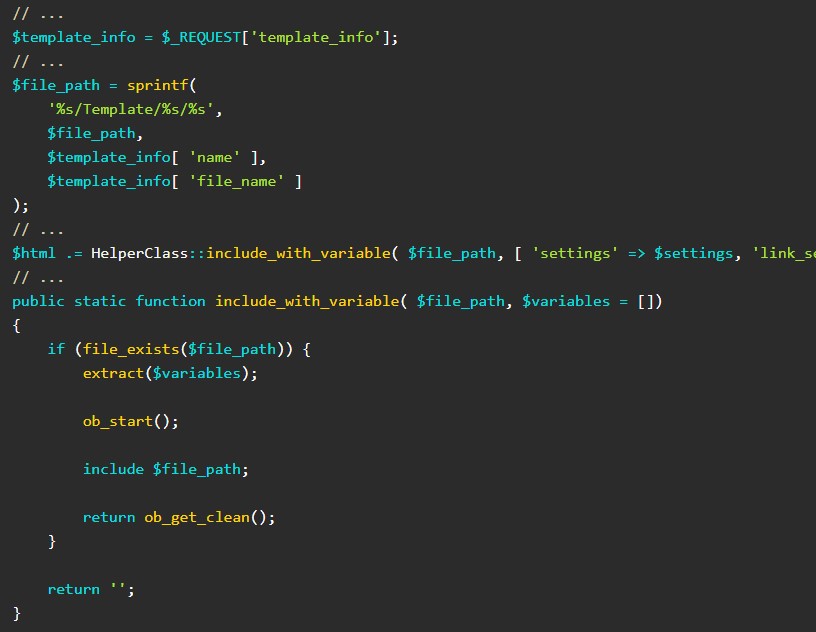
The flaw permits an unauthenticated person to carry out a neighborhood file inclusion assault, resembling a PHP file, to execute code on the location.
“The native file inclusion vulnerability exists because of the manner person enter information is used within PHP’s embrace operate which can be a part of the ajax_load_more and ajax_eael_product_gallery features.” explains PatchStack researchers who found the vulnerability.
The one prerequisite for the assault is for the location to have the “dynamic gallery” and “product gallery” widgets enabled in order that a none token examine is current.
Supply: Patchstack
Two failed patching makes an attempt
Researcher Wai Yan Muo Thet found the vulnerability on January 25, 2022, and the plugin developer already knew about its existence at the moment.
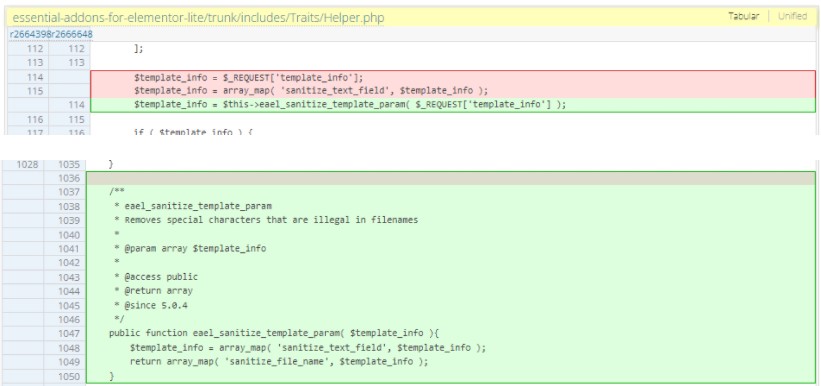
In reality, the creator had launched model 5.0.3 to deal with this subject by making use of a “sanitize_text_field” operate on the person enter information. Nevertheless, this sanitization would not forestall the inclusion of native payloads.
The second try was model 5.0.4, which added the “sanitize_file_name” operate and tried to take away particular characters, dots, slashes, and something that may very well be used for overriding the textual content sanitization step.
Supply: Patchstack
This was the model that Patchstack examined and located weak, so that they knowledgeable the developer that the repair hadn’t mitigated the problem sufficiently.
Finally, the creator launched model 5.0.5 that carried out PHP’s “realpath” operate, stopping malicious pathname resolutions.
Replace and mitigate
This model was launched final week, on January 28, 2022, and at the moment has solely been put in roughly 380,000 instances in keeping with WordPress’ obtain statistics.
With the plugin put in in over 1 million WordPress websites, which means there are over 600K websites that haven’t utilized the safety replace but.
In case you are among the many many who use Important Addons for Elementor, you may get the newest model from right here or apply the replace instantly from the WP dashboard.
To stop actors from leveraging native file inclusion flaws even after they cannot be instantly mitigated, observe these steps:
- Save your file paths in a safe database and provides an ID for each single one.
- Use verified and secured allowlist information and ignore the whole lot else.
- Do not embrace information on an online server that may be compromised, however use a database as an alternative.
- Make the server ship obtain headers routinely as an alternative of executing information in a specified listing.
[ad_2]