[ad_1]
Two weeks after particulars emerged a couple of second knowledge wiper pressure delivered in assaults towards Ukraine, yet one more damaging malware has been detected amid Russia’s persevering with navy invasion of the nation.
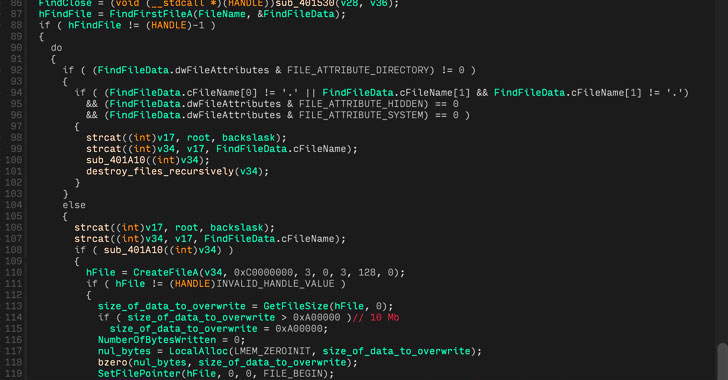
Slovak cybersecurity firm ESET dubbed the third wiper “CaddyWiper,” which it stated it first noticed on March 14 round 9:38 a.m. UTC. Metadata related to the executable (“caddy.exe“) exhibits that the malware was compiled at 7:19 a.m. UTC, a little bit over two hours previous to its deployment.
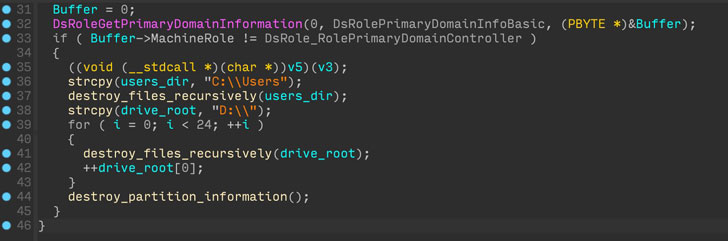
“This new malware erases consumer knowledge and partition data from hooked up drives,” the corporate stated in a tweet thread. “ESET telemetry exhibits that it was seen on a number of dozen techniques in a restricted variety of organizations.”
CaddyWiper is notable for the truth that it would not share any similarities with beforehand found wipers in Ukraine, together with HermeticWiper (aka FoxBlade or KillDisk) and IsaacWiper (aka Lasainraw), the 2 of which have been deployed in techniques belonging to authorities and industrial entities.
In contrast to CaddyWiper, each the HermeticWiper and IsaacWiper malware households are stated to have been in improvement for months upfront earlier than their launch, with oldest recognized samples compiled on December 28 and October 19, 2021, respectively.
However the newly found wiper shares one tactical overlap with HermeticWiper in that the malware, in a single occasion, was deployed through the Home windows area controller, indicating that the attackers had taken management of the Lively Listing server.
“Curiously, CaddyWiper avoids destroying knowledge on area controllers,” the corporate stated. “That is most likely a manner for the attackers to maintain their entry contained in the group whereas nonetheless disturbing operations.”
Microsoft, which has attributed the HermeticWiper assaults to a menace cluster tracked as DEV-0665, stated the “meant goal of those assaults is the disruption, degradation, and destruction of focused sources” within the nation.
The event additionally arrives as cybercriminals have opportunistically and more and more capitalized on the battle to design phishing lures, together with themes of humanitarian help and numerous sorts of fundraising, to ship quite a lot of backdoors comparable to Remcos.
“The worldwide curiosity within the ongoing conflict in Ukraine makes it a handy and efficient information occasion for cybercriminals to use,” Cisco Talos researchers stated. “If a sure matter of lure goes to extend the possibilities of a possible sufferer putting in their payload, they are going to use it.”
Nevertheless it’s not simply Ukraine that is been on the receiving finish of wiper assaults. Final week, cybersecurity agency Pattern Micro disclosed particulars of a .NET-based wiper referred to as RURansom that has solely focused entities in Russia by encrypting the recordsdata with a randomly generated cryptographic key.
“The keys are distinctive for every encrypted file and will not be saved wherever, making the encryption irreversible and marking the malware as a wiper fairly than a ransomware variant,” the researchers famous.
[ad_2]