[ad_1]
A financially-motivated malware marketing campaign has compromised over 800 WordPress web sites to ship a banking trojan dubbed Chaes concentrating on Brazilian clients of Banco do Brasil, Loja Integrada, Mercado Bitcoin, Mercado Livre, and Mercado Pago.
First documented by Cybereason in November 2020, the info-stealing malware is delivered through a classy an infection chain that is engineered to reap delicate client data, together with login credentials, bank card numbers, and different monetary data.
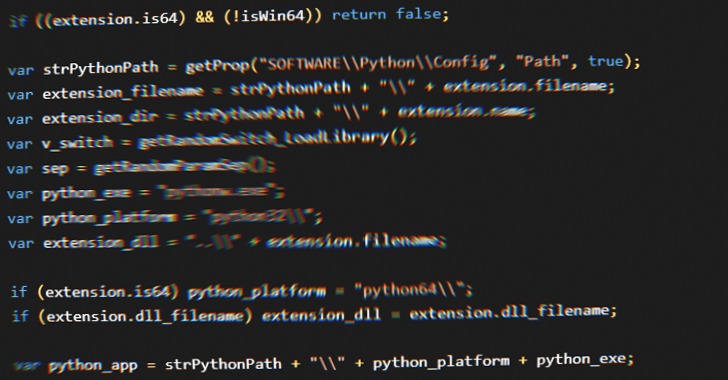
“Chaes is characterised by the multiple-stage supply that makes use of scripting frameworks corresponding to JScript, Python, and NodeJS, binaries written in Delphi, and malicious Google Chrome extensions,” Avast researchers Anh Ho and Igor Morgenstern mentioned. “The last word objective of Chaes is to steal credentials saved in Chrome and intercept logins of common banking web sites in Brazil.”
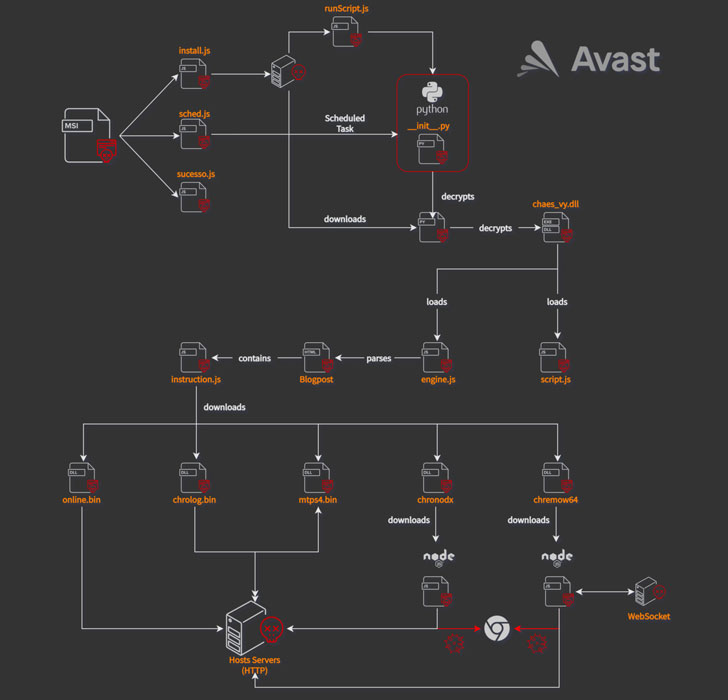
The assault sequence is triggered when customers go to one of many contaminated web sites, upon which a pop-up is displayed, urging them to put in a pretend Java Runtime utility. Ought to the consumer observe by way of the directions, the rogue installer initiates a posh malware supply routine that culminates within the deployment of a number of modules.
Among the middleman payloads usually are not solely encrypted but additionally hidden as commented-out code contained in the HTML web page of a Blogger blogspot area (“awsvirtual[.]blogspot.com”). Within the last stage, a JavaScript dropper downloads and installs as many as 5 Chrome extensions —
- On-line – A Delphi module used to fingerprint the sufferer and transmit the system data to a command-and-control (C2) server
- Mtps4 (MultiTela Pascal) – A Delphi-based backdoor whose fundamental objective is to hook up with the C2 server and look ahead to a responding Pascal Script to execute
- Chrolog (ChromeLog) – A Google Chrome password stealer written in Delphi
- Chronodx (Chrome Noder) – A JavaScript trojan that, upon detecting the launch of Chrome browser by the sufferer, closes it instantly and reopens its personal occasion of Chrome containing a malicious module that steals banking data
- Chremows (Chrome WebSocket) – A JavaScript banking trojan that data keypresses and mouse clicks on Chrome with the objective of plundering login credentials from customers of Mercado Livre and Mercado Pago
Stating that the assaults are ongoing, Avast mentioned that it had shared its findings with the Brazilian CERT to disrupt the malware’s unfold. That mentioned, Chaes-related artifacts proceed to stay on a number of the contaminated web sites.
“Chaes exploits many web sites containing CMS WordPress to serve malicious installers,” the researchers concluded. “The Google Chrome extensions are capable of steal customers’ credentials saved in Chrome and accumulate customers’ banking data from common banking web sites.”
[ad_2]