COVID Does Not Unfold to Computer systems
“…properly, in fact!” is what you may assume. It is a organic risk, so how may it have an effect on digital belongings?
However cling on. Amongst different results, this pandemic has caused a large shift in a number of technological areas. Not solely did it power quite a few organizations – that to date have been reluctant – to gear up in cyber to go digital, suddenly, oftentimes with swiftly pieced collectively methods.
It additionally made distant working (and the concerned instruments) develop in double-digits, inflicting the great previous perimeter (which was already in a questionable state as a consequence of cloud adaption) to be principally shattered. The workplace is now wherever. And which means entry to information must be all over the place too.
Conserving all of this in thoughts, the overall assumption was that within the wake of the pandemic we might face a digital nightmare with susceptible customers, compromised company networks en masse and the top of the (digital) world. However let us take a look at some attention-grabbing numbers of what really occurred.
Are hackers locked down too?
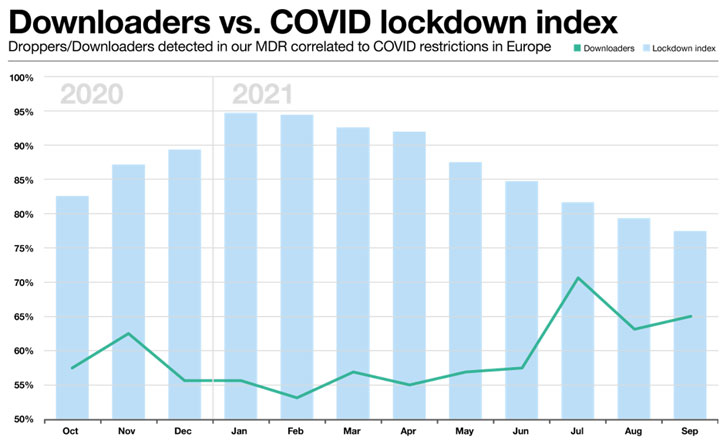
Let’s check out the variety of droppers we noticed in our MDR information and correlate it with different information we’ve got relating to the depth of COVID lockdown restrictions over time, Droppers are a superb total indicator of malicious exercise, as they usually point out an early stage of an assault (which in fact we attempt to forestall in getting any additional).
The COVID stringency index[1] mirrored within the bar chart involves us from Oxford College and is a composite measure based mostly on 9 response indicators, together with college closures, office closures, and journey bans, rescaled to a price from 0 to 100. In different phrases, the nearer the bar is to 100, the extra extreme the restrictions at the moment. We have averaged the indices for the Nordics, Benelux, Germany, France, the UK and South Africa, which symbolize the majority of our operational space.
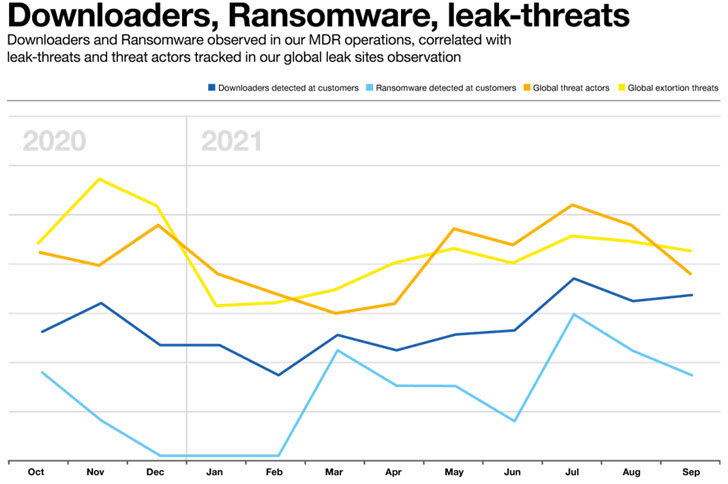
It is also attention-grabbing to correlate the info we’ve got from our Menace Detection companies, with information we’ve got from observing cyber extortion’ leak websites’ (which we’ve got already written about earlier).
A number of observations emerge from an examination of the charts above:
We observe a particular lower in confirmed downloader exercise within the months of November and December 2020 after the Trickbot botnet was taken down by legislation enforcement, and in January and February 2021, instantly after Emotet was taken down. After these two occasions, downloader exercise will increase steadily till peaking over the European trip interval in July.
There does look like a unfastened correlation between downloaders – which symbolize the beginning of the cyber kill chain – and confirmed ransomware exercise – which represents the final part of the kill chain, which is what one would count on.
Downloader and Ransomware actions each seem to extend over main vacation intervals – Easter and mid-summer. We do not see such a spike over Christmas 2020, however that may be due to the disruptive impression of the Trickbot and Emotet takedowns we alluded to earlier.
Usually, there seems to be an inverse correlation between the stringency of COVID lockdowns and the volumes of downloader exercise. The extra stringent the lockdowns, the much less of this exercise we see. This basic remark seems to carry for different types of malware exercise additionally. As we had already noticed in earlier analysis, this runs opposite to the prevailing narrative that assaults enhance when customers are working from dwelling.
It takes two to make a compromise
The conclusion right here seems to be, subsequently, that the quantity tendencies and patterns in malware exercise are overwhelmingly influenced by the patterns and behaviors of the potential victims, not the alternatives of the attacker. The exception could also be trip intervals, the place it seems that attackers might step their exercise up.
Legislation enforcement exercise has a notable impression, however this seems to be short-lived as a result of new actors and new instruments are inclined to pop up after one other one is taken down or a few of its members arrested.
So, the ultimate analysis? We are able to verify that truly COVID has not unfold to digital. At the least not within the deadly approach that was predicted. And that’s lastly some excellent news.
That is simply one other excerpt of the evaluation. Extra particulars just like the incident- and malware distribution throughout industries or enterprise sizes (in addition to a ton of different attention-grabbing analysis subjects) may be discovered within the Safety Navigator. It is accessible for obtain on the Orange Cyberdefense web site, so take a look. It is price it!
Be aware — This text was written and contributed by Diana Selck-Paulsson, Lead Safety Researcher at Orange Cyberdefense.