[ad_1]

Menace analysts have noticed a brand new marketing campaign named ‘OiVaVoii’, concentrating on firm executives and normal managers with malicious OAuth apps and customized phishing lures despatched from hijacked Workplace 365 accounts.
In accordance with a report from Proofpoint, the marketing campaign remains to be ongoing, although Microsoft is monitoring the exercise and has already blocked a lot of the apps.
The influence of government account takeovers ranges from lateral motion on the community and insider phishing to deploying ransomware and enterprise electronic mail compromise incidents.
Using OAuth apps
OAuth is an ordinary for token-based authentication and authorization, eradicating the necessity to enter account passwords.
Apps that use OAuth require particular permissions equivalent to file learn and write permissions, entry to calendar and electronic mail, and electronic mail ship authorization.
The aim of this method is to supply elevated usability and comfort whereas sustaining a excessive safety degree inside reliable environments by decreasing credential publicity.
With OAuth tokens, cloud-based third-party purposes can entry the info factors required to offer companies with productiveness options with out getting the customers’ passwords.
The actors behind the OiVaVoii marketing campaign used no less than 5 malicious OAuth purposes, 4 of them presently blocked: ‘Improve’, ‘Doc’, ‘Shared’, and ‘UserInfo’.
.jpg)
Supply: Proofpoint
Three of those apps have been created by verified publishers, which signifies that the risk actors compromised the account of a authentic Workplace tenant.
The risk actors then used the apps to ship out authorization requests to high-ranking executives within the focused organizations. In lots of instances, the recipients accepted the requests, seeing nothing suspicious in them.
When victims hit the Settle for button, the risk actors use the token to ship emails from their accounts to different staff inside the similar group.
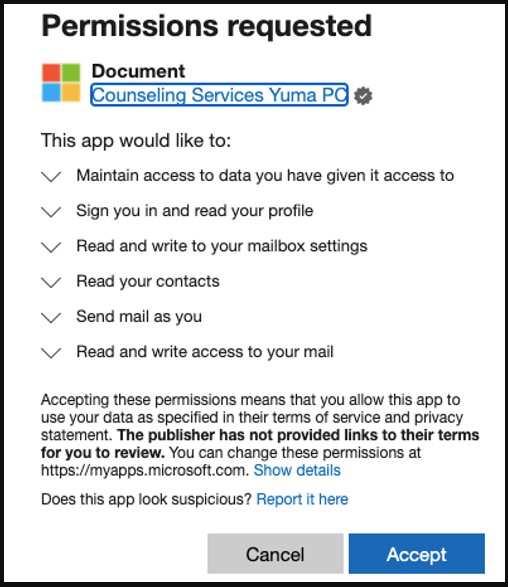
Supply: Proofpoint
In the event that they click on on Cancel, a manipulation within the Reply URL redirects them again to the consent display screen, locking them on the identical web page till they settle for the permission request.
Proofpoint additionally mentions the chance of man-in-the-middle proxy assaults that would additionally compromise the goal’s account credentials.
Marketing campaign remains to be lively
4 of the malicious OAuth apps utilized by the actors on this marketing campaign have been blocked, however new ones are being created and employed in the identical manner.
Additionally, executives who’ve already been compromised and given entry to their accounts stay high-risk factors for impacted organizations.
The doubtless compromised corporations have to revoke the permissions, delete the apps, take away any malicious mailbox guidelines added by the actors, and scan for any dropped information.
Lastly, all staff needs to be educated to suspect inner communications, particularly messages from high-ranking executives that don’t align with their commonplace enterprise practices.
[ad_2]


