[ad_1]
Microsoft has disclosed particulars of a large-scale, multi-phase phishing marketing campaign that makes use of stolen credentials to register units on a sufferer’s community to additional propagate spam emails and widen the an infection pool.
The tech large stated the assaults manifested by way of accounts that weren’t secured utilizing multi-factor authentication (MFA), thereby making it potential for the adversary to benefit from the goal’s bring-your-own-device (BYOD) coverage and introduce their very own rogue units utilizing the pilfered credentials.
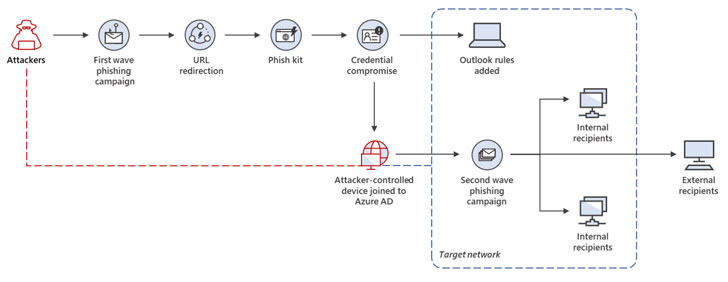
The assaults passed off in two levels. “The primary marketing campaign part concerned stealing credentials in goal organizations situated predominantly in Australia, Singapore, Indonesia, and Thailand,” Microsoft 365 Defender Risk Intelligence Staff stated in a technical report printed this week.
“Stolen credentials had been then leveraged within the second part, wherein attackers used compromised accounts to broaden their foothold throughout the group by way of lateral phishing in addition to past the community by way of outbound spam.”
The marketing campaign began with customers receiving a DocuSign-branded phishing lure containing a hyperlink, which, upon clicking, redirected the recipient to a rogue web site masquerading because the login web page for Workplace 365 to steal the credentials.
The credential theft not solely resulted within the compromise of over 100 mailboxes throughout completely different firms, but in addition enabled the attackers to implement an inbox rule to thwart detection. This was then adopted by a second assault wave that abused the dearth of MFA protections to enroll an unmanaged Home windows machine to the corporate’s Azure Lively Listing (AD) occasion and unfold the malicious messages.
By connecting the attacker-controlled machine to the community, the novel method made it viable to broaden the attackers’ foothold, covertly proliferate the assault, and transfer laterally all through the focused community.
“To launch the second wave, the attackers leveraged the focused person’s compromised mailbox to ship malicious messages to over 8,500 customers, each in and out of doors of the sufferer group,” Microsoft stated. “The emails used a SharePoint sharing invitation lure because the message physique in an try to persuade recipients that the ‘Fee.pdf’ file being shared was respectable.”
The event comes as email-based social engineering assaults proceed to be essentially the most dominant means for attacking enterprises to realize preliminary entry and drop malware on compromised techniques.
Earlier this month, Netskope Risk Labs disclosed a malicious marketing campaign attributed to the OceanLotus group that bypassed signature-based detections by utilizing non-standard file varieties similar to internet archive file (.MHT) attachments to deploy information-stealing malware.
Along with turning on MFA, implementing finest practices such nearly as good credential hygiene and community segmentation can “enhance the ‘value’ to attackers making an attempt to propagate by way of the community.”
“These finest practices can restrict an attacker’s skill to maneuver laterally and compromise belongings after preliminary intrusion and must be complemented with superior safety options that present visibility throughout domains and coordinate menace information throughout safety elements,” Microsoft added.
[ad_2]