[ad_1]
A brand new, refined phishing assault has been noticed delivering the AsyncRAT trojan as a part of a malware marketing campaign that is believed to have commenced in September 2021.
“By a easy electronic mail phishing tactic with an html attachment, menace attackers are delivering AsyncRAT (a distant entry trojan) designed to remotely monitor and management its contaminated computer systems by a safe, encrypted connection,” Michael Dereviashkin, safety researcher at enterprise breach prevention agency Morphisec, mentioned in a report.
The intrusions start with an electronic mail message containing an HTML attachment that is disguised as an order affirmation receipt (e.g., Receipt-<digits>.html). Opening the decoy file redirects the message recipient to an online web page prompting the person to save lots of an ISO file.
However not like different assaults that route the sufferer to a phishing area arrange explicitly for downloading the next-stage malware, the most recent RAT marketing campaign cleverly makes use of JavaScript to regionally create the ISO file from a Base64-encoded string and mimic the obtain course of.
“The ISO obtain isn’t generated from a distant server however from inside the sufferer’s browser by a JavaScript code that is embedded contained in the HTML receipt file,” Dereviashkin defined.
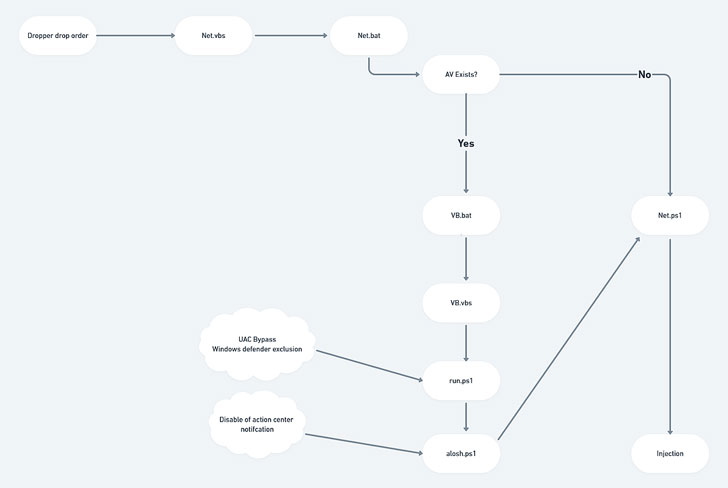
When the sufferer opens the ISO file, it’s routinely mounted as a DVD Drive on the Home windows host and contains both a .BAT or a .VBS file, which continues the an infection chain to retrieve a next-stage element through a PowerShell command execution.
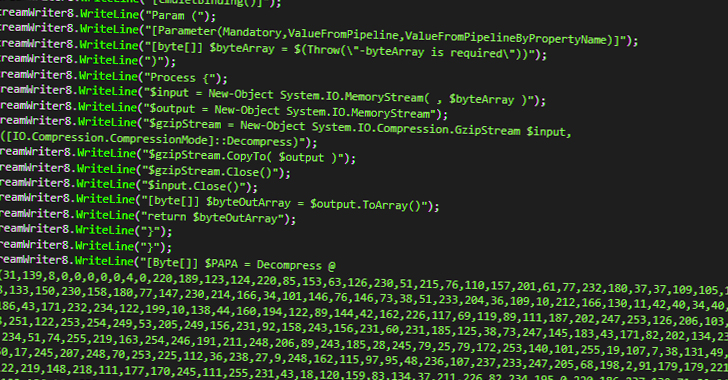
This ends in the execution of a .NET module in-memory that subsequently acts as a dropper for 3 recordsdata — one appearing as a set off for the following — to lastly ship AsyncRAT as the ultimate payload, whereas additionally checking for antivirus software program and establishing Home windows Defender exclusions.
RATs corresponding to AsyncRAT are usually used to forge a distant hyperlink between a menace actor and a sufferer machine, steal info, and conduct surveillance by microphones and cameras. They supply an array of superior capabilities that give the attackers the flexibility to totally monitor and management the compromised machines.
Morphisec additionally identified the marketing campaign’s superior ways, which it mentioned allowed the malware to slide by nearly undetected by most antimalware engines regardless of the operation being in impact for shut to 5 months.
[ad_2]