[ad_1]
A beforehand undocumented malware packer named DTPacker has been noticed distributing a number of distant entry trojans (RATs) and data stealers resembling Agent Tesla, Ave Maria, AsyncRAT, and FormBook to plunder data and facilitate follow-on assaults.
“The malware makes use of a number of obfuscation strategies to evade antivirus, sandboxing, and evaluation,” enterprise safety firm Proofpoint stated in an evaluation printed Monday. “It’s seemingly distributed on underground boards.”
The .NET-based commodity malware has been related to dozens of campaigns and a number of risk teams, each superior persistent risk (APT) and cybercrime actors, since 2020, with the intrusions geared toward a whole lot of consumers throughout many sectors.
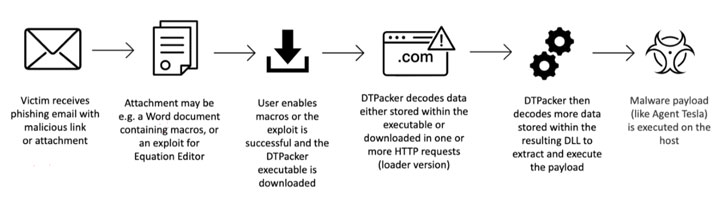
Assault chains involving the packer depend on phishing emails as an preliminary an infection vector. The messages include a malicious doc or a compressed executable attachment, which, when opened, deploys the packer to launch the malware.
Packers differ from downloaders in that in contrast to the latter, they carry an obfuscated payload to cover their true conduct from safety options in a way that acts as an “armor to guard the binary” and make reverse engineering tougher.
What makes DTPacker completely different is that it capabilities as each. Its identify is derived from the truth that it used two Donald Trump-themed fastened keys — “trump2020” and “Trump2026” — to decode the embedded or downloaded useful resource that finally extracts and executes the ultimate payload.
It is presently not recognized why the authors selected this particular reference to the previous U.S. president because the malware is neither used to focus on politicians or political organizations nor are the keys seen by the focused victims.
Proofpoint stated it noticed the operators making refined adjustments by switching to utilizing soccer fan membership web sites as decoys to host the malware from March 2021, with the packer employed by teams like TA2536 and TA2715 in their very own campaigns a yr earlier than that.
“DTPacker’s use as each a packer and downloader and its variation in supply and obfuscation while protecting two such distinctive keys as a part of its decoding could be very uncommon,” stated the researchers, who count on the malware for use by a number of risk actors for the foreseeable future.
[ad_2]