[ad_1]
2021 was a 12 months peppered by cyberattacks, with quite a few knowledge breaches occurring. Not solely that, however ransomware has additionally change into a distinguished participant within the hackers’ world.
Now, greater than ever, it is vital for enterprises to step up cybersecurity measures. They’ll do that by way of a number of items of know-how, comparable to an open-source safety platform like Wazuh.
Wazuh is a free and open supply safety platform that unifies XDR and SIEM capabilities, which not solely permits corporations to detect refined threats, however can even assist immensely in stopping knowledge breaches and leaks from occurring. In consequence, it will probably save companies from pricey fixes that may in the end finish of their closure.
It is usually attainable to combine Wazuh with various exterior providers and instruments. A few of them are VirusTotal, YARA, Amazon Macie, Slack, and Fortigate Firewall. Consequently, corporations can enhance their safety towards hackers from penetrating their networks.
What’s nice about Wazuh is that it is scalable, open supply and free. It could actually compete with many high-end cybersecurity options which are accessible for some huge cash. So this might help SMEs immensely budget-wise.
Learn on to search out out extra on how Wazuh might help with cybersecurity for companies.
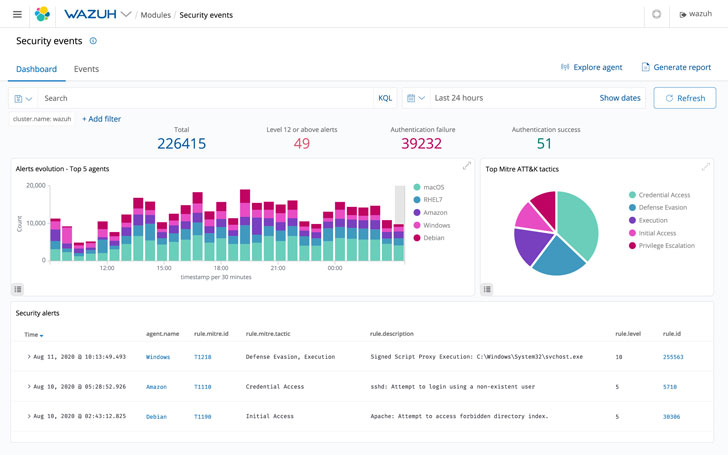
Safety Analytics
Wazuh routinely collects and aggregates safety knowledge from programs working Linux, Home windows, macOS, Solaris, AIX, and different working programs within the monitored area, making it a particularly complete SIEM answer.
However extra importantly, Wazuh additionally analyzes and correlates knowledge with the intention to detect anomalies and intrusions. Such a intelligence means there’s early menace detection in numerous environments.
For instance, Wazuh can be utilized within the workplace, in addition to in cloud environments so distant staff can nonetheless reap the advantages of Wazuh. Enhancing digital safety will not should be restricted to only a brick-and-mortar setting.
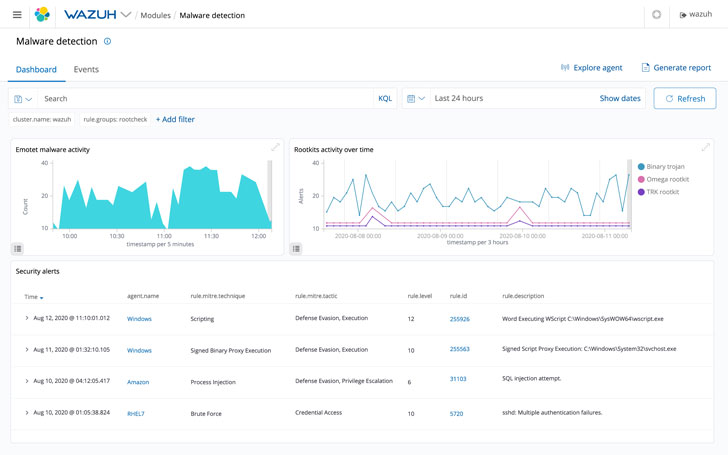
Intrusion Detection
Wazuh software program has multi-platform brokers that monitor programs, detect threats, and set off automated responses as wanted. Extra particularly, they hone in on rootkits and malware, in addition to suspicious anomalies.
As well as, these brokers can detect stealth know-how like hidden recordsdata, cloaked processes, and unregistered community listeners.
On high of those capabilities for intrusion detection, Wazuh’s server has a signature-based method. It analyzes collected log knowledge and might decide factors of compromise by evaluating them with identified signatures.
This characteristic can instantly decide and stop workers from downloading and putting in malicious functions.
This offers workplaces a security web. Worker training on cybersecurity needs to be the primary line of protection, in any case.
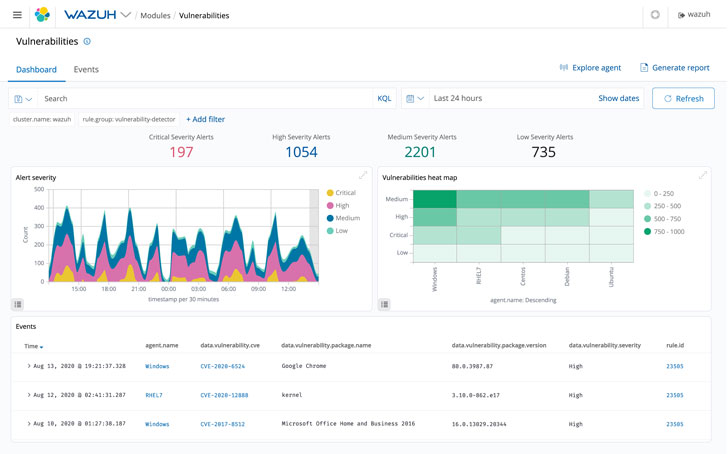
Vulnerability Detection
Wazuh can even pinpoint the place community vulnerabilities are. This permits enterprises to search out their weakest hyperlinks and plug up holes earlier than cybercriminals can exploit them first.
Wazuh brokers will pull software program stock knowledge and ship it to their server. Right here, it is in contrast with constantly up to date widespread vulnerabilities and publicity (CVE) databases. In consequence, these brokers will discover and determine any software program that is susceptible.
In lots of circumstances, antivirus software program can deal with these vulnerabilities. These applications launch safety patches regularly.
However in uncommon circumstances, antivirus builders will not discover vulnerabilities in time. Or they may not discover them in any respect, which might go away companies uncovered. Having Wazuh means companies get an additional set of eyes to make sure their cybersecurity is hermetic.
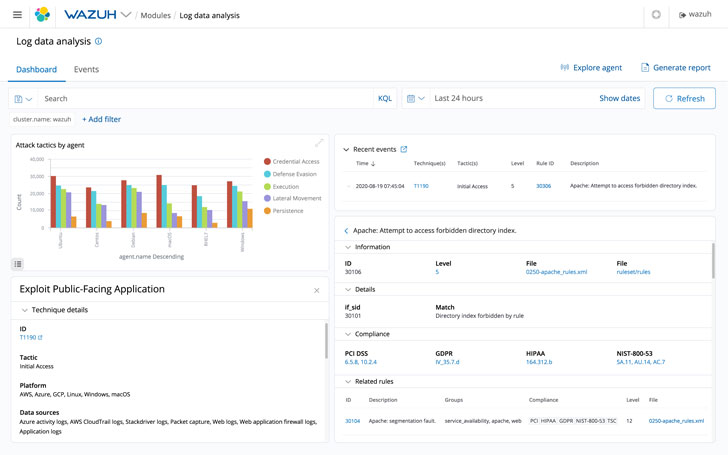
Log Knowledge Evaluation
Not solely does Wazuh acquire community knowledge and utility logs, however it additionally securely sends them to a central supervisor for rule-based evaluation and storage.
This evaluation of log knowledge is predicated on over 3000 totally different guidelines that determine something that has gone flawed, whether or not it’s an outdoor drive or consumer error. For instance, the principles in place can detect utility or system errors, coverage violations, misconfigurations, in addition to tried or profitable malicious exercise.
As well as, the log knowledge evaluation can pinpoint each tried and profitable malicious actions. Early detection is essential in maintaining networks secure.
Enterprises can be taught from tried malicious actions and improve their cybersecurity accordingly.
And for profitable malicious actions, the system can shortly quarantine contaminated recordsdata. Or they’ll delete them earlier than they’ll do extra injury.
One other factor the log knowledge evaluation can present is coverage violations. Whether or not they’re intentional or unintentional, these violations might be dropped at administration’s consideration. Then, they’ll take swift motion to rectify the state of affairs.
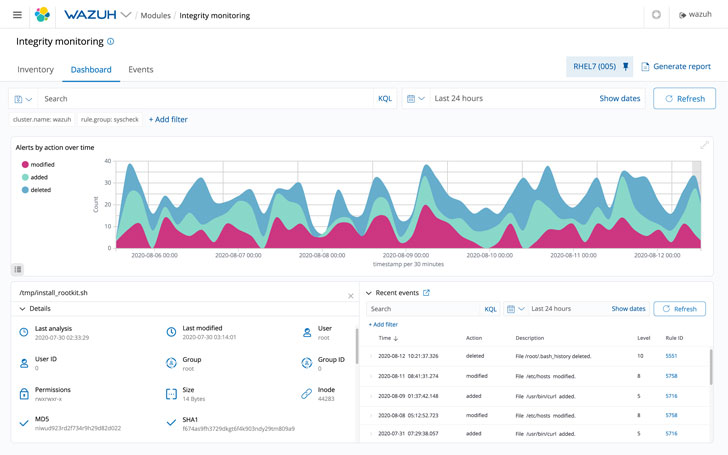
File Integrity Monitoring
Wazuh’s File integrity monitoring (FIM) characteristic might be configured to scan chosen recordsdata or directories periodically and alert the consumer when any modifications are detected. Not solely does it preserve observe of which customers create and modify recordsdata, however it additionally tracks which functions are used and when possession is modified.
Due to the extent of element from file integrity monitoring, companies will be capable of know precisely when threats are available in. They will additionally determine compromised hosts immediately.
For example, ransomware is now rampant, however Wazuh might help forestall and detect this menace. Ought to a hacker try phishing, the safety monitoring will decide up on the malicious recordsdata which have snuck in. It’s going to detect new recordsdata created, in addition to any unique recordsdata eliminated.
Ought to there be a excessive variety of these situations, the file integrity monitoring will flag it as a attainable ransomware assault. Be aware that customized guidelines needs to be created for this to occur.
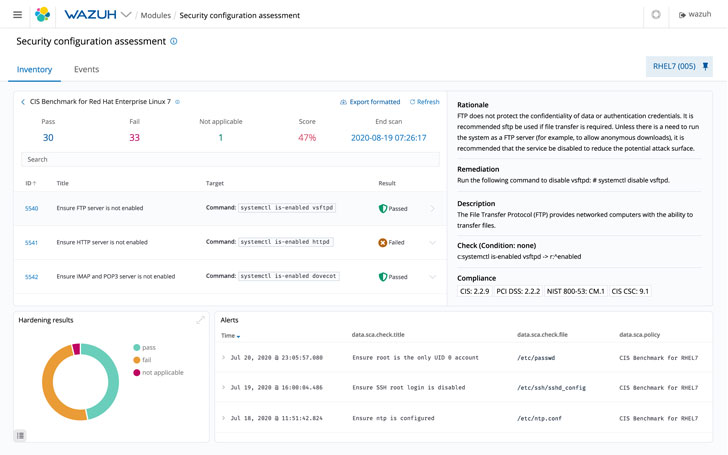
Configuration Evaluation
Safety compliance is crucial to enhance a company’s safety posture and scale back its assault floor. However it may be each time-consuming and difficult. Fortuitously, Wazuh can help with it.
Wazuh’s Automated Safety Configuration Evaluation (SCA) appears for misconfigurations and helps keep an ordinary configuration throughout all monitored endpoints.
As well as, Wazuh brokers additionally scan functions which are identified to be susceptible, unpatched or configured insecurely. That method, the strongest cybersecurity partitions are up always.
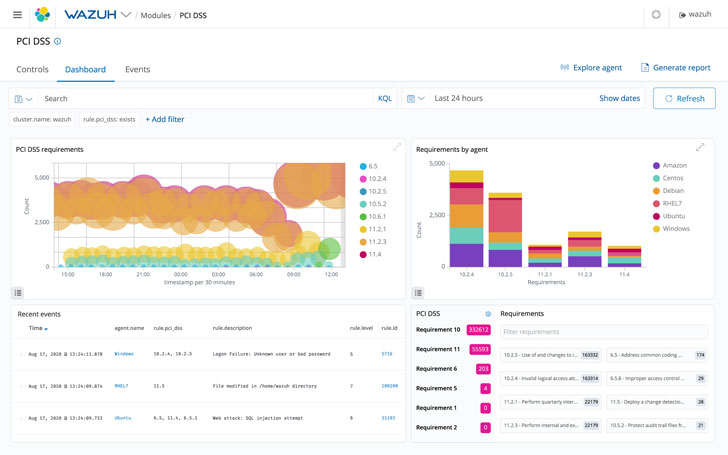
Regulatory Compliance
On the subject of compliance, the regulatory compliance characteristic additionally helps customers sustain with requirements and laws. Extra importantly, it permits companies to scale and combine different platforms.
Wazuh generates reviews with its internet consumer interface. There are additionally a number of dashboards to allow customers to handle all platforms from one place. If the brokers discover something that is non-compliant, the customers are immediately alerted.
Its ease of use lets many monetary corporations meet Fee Card Trade Knowledge Safety Normal (PCI DSS) necessities. This contains cost processing corporations, too.
These within the healthcare trade can have peace of thoughts understanding they’re HIPAA-compliant. And for individuals who cope with European knowledge, they will be GDPR-compliant as effectively.
Incident Response
Incident response is a really helpful characteristic of Wazuh for lively threats. There are out-of-the-box lively responses, which suggests the consumer does not should do something to set them up. Ought to the system detect lively threats, countermeasures leap into motion immediately.
For instance, many hackers use brute-force assaults to guess username and password mixtures. Wazuh will pay attention to every failed authentication try.
With sufficient failures, the system will acknowledge them as a part of a brute-force assault. As a result of a sure criterion is met (e.g., 5 failed login makes an attempt), it’ll block that IP tackle from additional makes an attempt. This implies not solely can Wazuh decide up on brute-force assaults, however it will probably additionally shut them down.
Moreover, customers can use it to run distant instructions and system queries. They’ll additionally remotely determine indicators of compromise (IOCs).
This permits third events to run stay forensics and incident response duties. In consequence, this opens up alternatives to work with extra professionals who can safeguard firm knowledge.
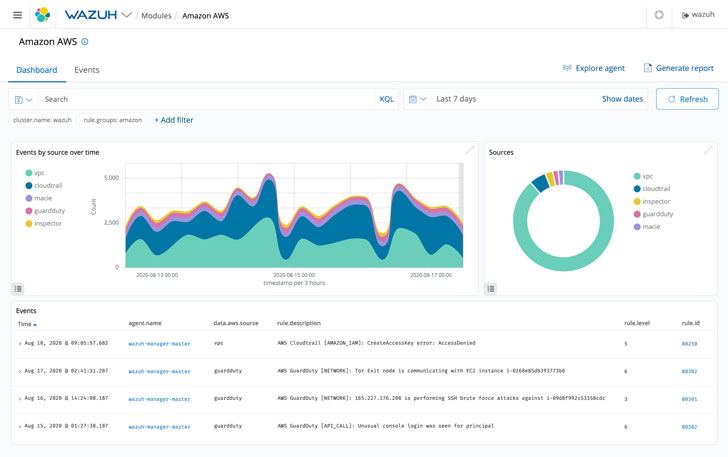
Cloud Safety
Right now, many workplaces use the cloud to retailer recordsdata. This permits workers to entry them from all around the world, as long as they’ve an web connection.
However with this comfort comes a brand new safety concern. Anybody with an web connection can presumably hack the cloud and achieve entry to delicate knowledge.
Wazuh makes use of integration modules, which pull safety knowledge from well-known cloud suppliers, comparable to Amazon AWS, Microsoft Azure or Google Cloud. As well as, it units guidelines for a consumer’s cloud surroundings to identify potential weaknesses.
It really works equally to the vulnerability detection operate. It’s going to alert customers to intrusion makes an attempt, system anomalies, and unauthorized consumer actions.
Containers Safety
Wazuh’s containers safety characteristic supplies cyber menace intelligence for Docker hosts, Kubernetes nodes and containers. Once more, it’ll discover system anomalies, vulnerabilities, and threats.
The agent’s native integration means customers do not should arrange connections with their Docker hosts and containers. It’s going to preserve amassing and analyzing knowledge. It’s going to additionally present customers with steady monitoring of working containers.
Wazuh is a Should for Enterprises
Because the digital world retains evolving, so do cybercriminals. Due to this fact, maintaining with cybersecurity measures and investing in top-of-the-line intrusion detection is crucial.
Wazuh combines all of those options in a single platform, making it a strong instrument for analysts in addition to an actual drive multiplier for overburdened IT employees.
Comparatively to different options, Wazuh routinely provides related context to alerts and analyses, permits higher decision-making, and assists in bettering compliance and threat administration.
When mixed with vulnerability detection, file integrity monitoring, and configuration evaluation, Wazuh can help enterprises in staying one step forward of hackers.
By investing time and assets into this free platform, companies can construct extra layers to their cybersecurity measures. And in return, they’ll set themselves up for safer networks for years to return.
Wazuh integrations
Beneath there are a number of hyperlinks the place you possibly can see how Wazuh might be built-in with totally different functions and software program and the way capabilities might be prolonged with these integrations:
[ad_2]