[ad_1]
Researchers have disclosed three safety vulnerabilities affecting Pascom Cloud Telephone System (CPS) that may very well be mixed to realize a full pre-authenticated distant code execution of affected techniques.
Kerbit safety researcher Daniel Eshetu mentioned the shortcomings, when chained collectively, can result in “an unauthenticated attacker gaining root on these units.”
Pascom Cloud Telephone System is an built-in collaboration and communication answer that permits companies to host and arrange non-public phone networks throughout completely different platforms in addition to facilitate the monitoring, upkeep, and updates related to the digital cellphone techniques.
The set of three flaws consists of these stemming from an arbitrary path traversal within the internet interface, a server-side request forgery (SSRF) attributable to an outdated third-party dependency (CVE-2019-18394), and a post-authentication command injection utilizing a daemon service (“exd.pl”).
In different phrases, the vulnerabilities might be stringed in a chain-like trend to entry non-exposed endpoints by sending arbitrary GET requests to acquire the administrator password, after which use it to realize distant code execution utilizing the scheduled activity.
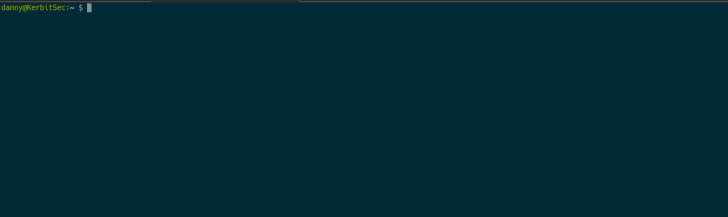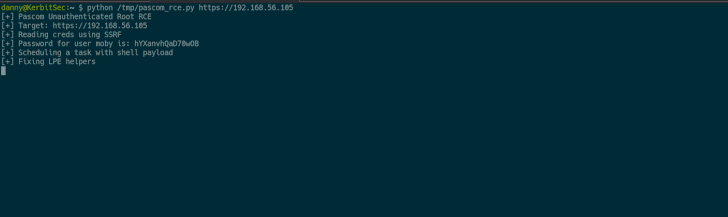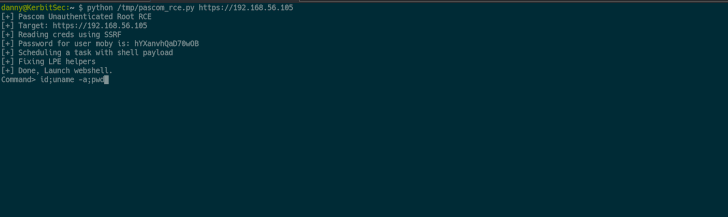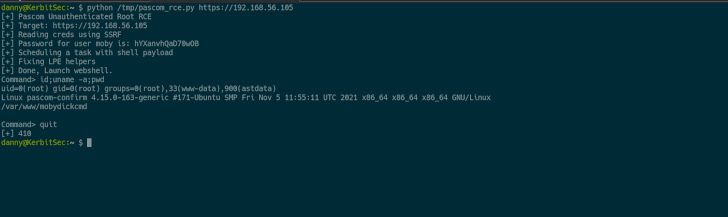
The exploit chain can be utilized “to execute instructions as root,” Eshetu mentioned, including, “this provides us full management of the machine and a simple method to escalate privileges.” The failings had been reported to Pascom on January 3, 2022, following which patches have been launched.
Prospects who’re self-hosting CPS versus on the cloud are suggested to replace to the most recent model (pascom Server 19.21) as quickly as attainable to counter any potential threats.
[ad_2]