[ad_1]

LockBit is the newest ransomware gang whose Linux encryptor has been found to be specializing in the encryption of VMware ESXi digital machines.
The enterprise is more and more transferring to digital machines to save lots of pc sources, consolidate servers, and for simpler backups.
Resulting from this, ransomware gangs have developed their techniques to create Linux encryptors that particularly goal the favored VMware vSphere and ESXi virtualization platforms over the previous 12 months.
Whereas ESXi just isn’t strictly Linux, it does share lots of its traits, together with the flexibility to run ELF64 Linux executables.
Lockbit targets VMware ESXi servers
In October, LockBit started selling the brand new options of their Ransomware-as-a-Service operation on the RAMP hacking boards, together with a brand new Linux encryptor that targets VMware ESXi digital machines.
In a brand new report, Development Micro researchers analyzed the ransomware gang’s Linux encryptor and defined the way it’s used to focus on VMWare ESXi and vCenter installations.
Linux encryptors are nothing new, with BleepingComputer reporting on related encryptors up to now from HelloKitty, BlackMatter, REvil, AvosLocker, and the Hive ransomware operations.
Like different Linux encryptors, LockBits offers a command-line interface permitting associates to allow and disable varied options to tailor their assaults.
These options embrace the flexibility to specify how massive a file and what number of bytes to encrypt, whether or not to cease operating digital machines, or wipe free area after, as proven by the picture under.
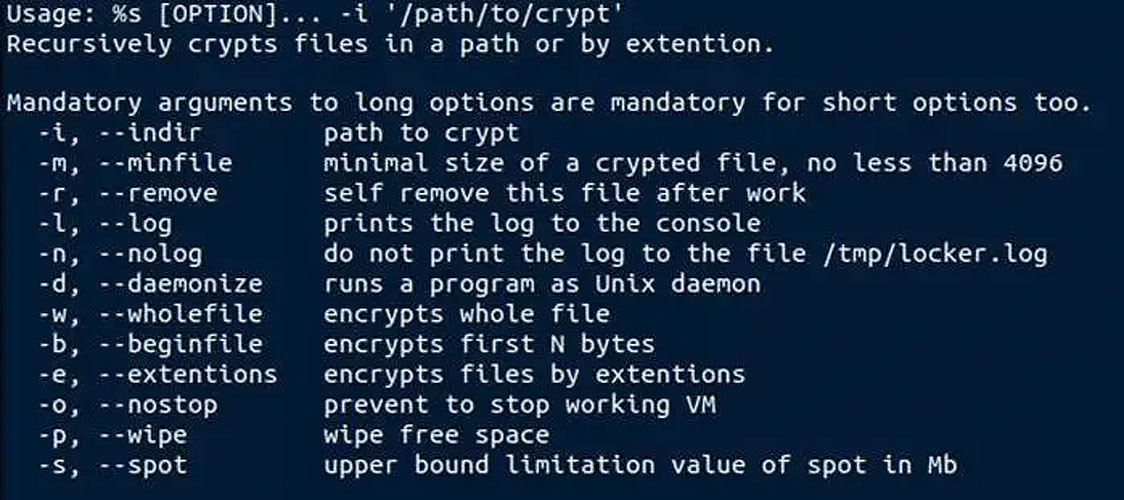
Supply: Development Micro
Nonetheless, what makes the LockBit linux encryptor stand out is the broad use of each VMware ESXI and VMware vCenter command-line utilities to verify what digital machines are operating and to shut them down cleanly so they aren’t corrupted whereas being encrypted.
The complete checklist of instructions seen by Development Micro in LockBit’s encryptor are listed under:
| Command | Description |
|---|---|
| vm-support –listvms | Get hold of an inventory of all registered and operating VMs |
| esxcli vm course of checklist | Get an inventory of operating VMs |
| esxcli vm course of kill –type drive –world-id | Energy off the VM from the checklist |
| esxcli storage filesystem checklist | Test the standing of knowledge storage |
| /sbin/vmdumper %d suspend_v | Droop VM |
| vim-cmd hostsvc/enable_ssh | Allow SSH |
| vim-cmd hostsvc/autostartmanager/enable_autostart false | Disable autostart |
| vim-cmd hostsvc/hostsummary grep cpuModel | Decide ESXi CPU mannequin |
Development Micro states that the encryptor makes use of AES to encrypt recordsdata and elliptic-curve cryptography (ECC) algorithms to encrypt the decryption keys.
With the widespread use of VMware ESXI within the enterprise, all community defenders and safety skilled ought to count on that each massive ransomware operation has already developed a Linux variant.
By making this assumption, admins and safety professionals can create acceptable defenses and plans to guard all units of their networks, quite than simply Home windows units.
That is very true for the LockBit operation, which has turn out to be probably the most outstanding ransomware operation since REvil shut down and prides itself on its encryptors’ velocity and have set.
It’s also important to keep in mind that as a lot as we’re watching ransomware gangs, they’re additionally watching us again.
Which means that they monitor researchers’ and journalists’ social feeds for the newest techniques, defenses, and vulnerabilities that they will then use towards company targets.
Resulting from this, ransomware gangs are continually evolving their encryptions and techniques to try to keep one step forward of safety and Home windows admins.
[ad_2]