[ad_1]
An impartial safety researcher has obtained a $100,500 bug bounty from Apple after discovering a safety gap within the firm’s Safari browser for macOS that would permit a malicious web site to hijack accounts and seize management of customers’ webcams.
Georgia Institute of Expertise’s Ryan Pickren, who can be the founding father of BugPoC, uncovered a common cross-site scripting (UXSS) flaw in Apple’s Safari browser that would result in severe safety issues.
As Pickren explains in a technical weblog publish, the assault begins by tricking a possible sufferer into opening what they consider to be an innocent-looking .PNG picture file.
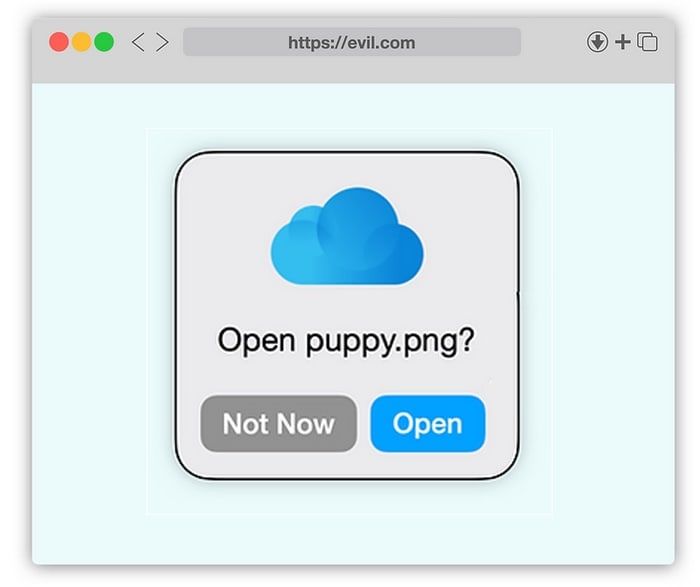
Nonetheless, by exploiting options constructed into Apple iCloud and Safari which are trusted by macOS, unsuspecting customers can find yourself with a malicious file operating on their Mac, somewhat than opening a innocent picture.
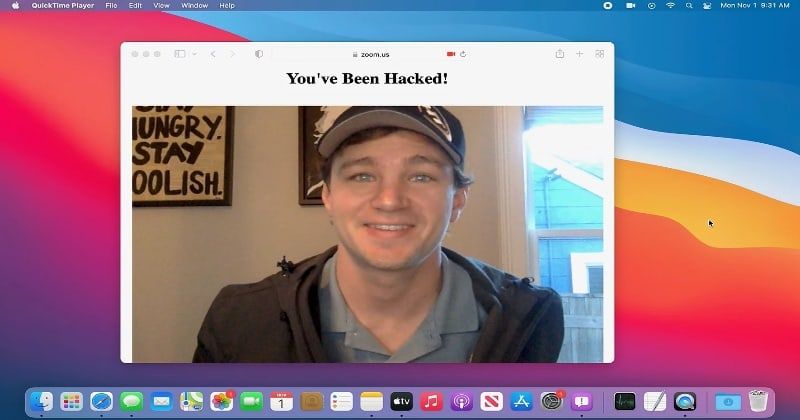
The tip result’s that an attacker may seize management of Safari, entry any accounts that the person is logged into, and even entry customers’ microphone and webcam.
In his weblog publish, Pickren describes how the UXSS assault could possibly be utilized by an assault to inject arbitrary code into web sites. For example, JavaScript could possibly be injected onto a trusted video chat web site like Zoom to activate the webcam.
In fact, such an assault does not forestall a Mac from displaying a inexperienced “on” mild beside their webcam, however you need to surprise how many individuals would discover.
As well as, and maybe extra conventionally, an attacker may entry any recordsdata saved regionally on the sufferer’s Mac.
Pickren’s discovery is ingenious, and he pieced collectively a wide range of flaws and options of macOS to “punch a gap within the browser”:
“…the bug offers the attacker full entry to each web site ever visited by the sufferer. Meaning along with turning in your digicam, my bug can even hack your iCloud, PayPal, Fb, Gmail, and so forth. accounts too.”
The excellent news is that there is no such thing as a indication that anybody found the flaw earlier than Pickren responsibly disclosed the issues to Apple in mid-July 2021. Safety patches have now been issued for all the vulnerabilities, stopping future exploitation.
The researcher seems to have, not less than partially, constructed his newest webcam hijack on the foundations of a earlier webcam-hijacking vulnerability he discovered a yr in the past, that netted him $75,000 from Apple.
As a scholar Pickren managed to earn 15 million air miles by means of the United airways’ bug bounty program, donating half to Georgia Tech and an additional 2.5 million extra to Make-A-Want America.
[ad_2]