
Microsoft seizes websites utilized by APT15 Chinese language state hackers

Microsoft seized at the moment dozens of malicious websites utilized by the Nickel China-based hacking group to focus on organizations within the US and 28 different international locations worldwide.
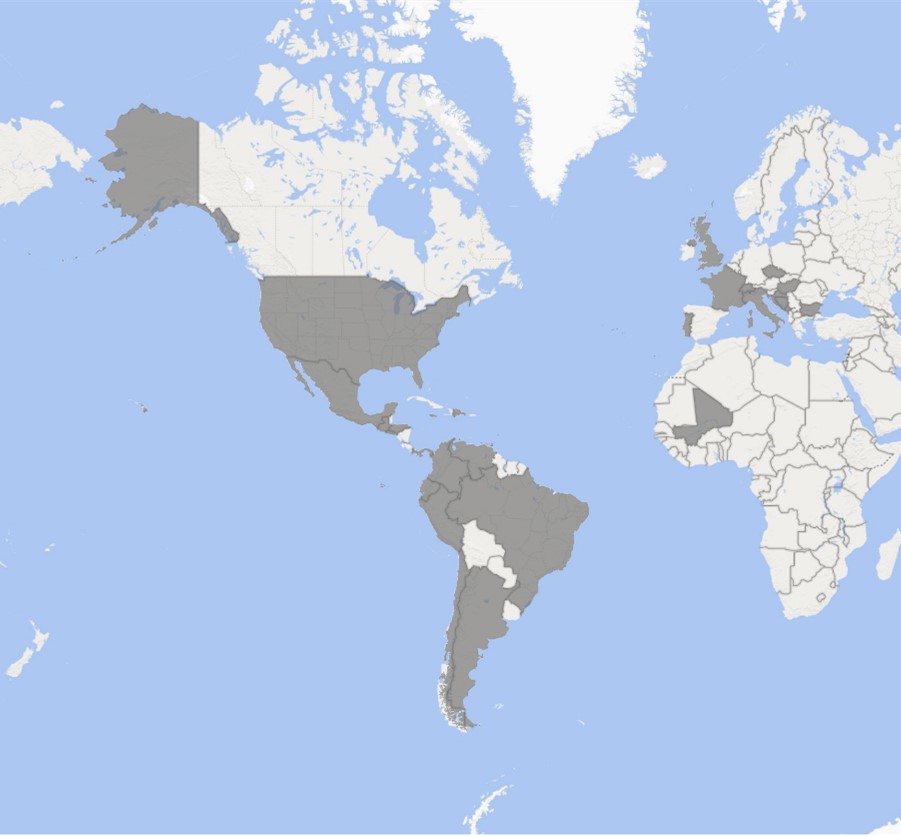
Of their assaults, the Nickel risk actor (additionally tracked as KE3CHANG, APT15, Vixen Panda, Royal APT, and Playful Dragon) compromised the servers of presidency organizations, diplomatic entities, and non-governmental organizations (NGOs) throughout 29 international locations, primarily from Europe and Latin America.
“Nickel has focused organizations in each the personal and public sectors, together with diplomatic organizations and ministries of overseas affairs in North America, Central America, South America, the Caribbean, Europe and Africa,” stated Tom Burt, Company Vice President for Buyer Safety & Belief at Microsoft.
“We consider these assaults had been largely getting used for intelligence gathering from authorities businesses, suppose tanks, and human rights organizations.”
Microsoft was in a position to take down Nickel’s infrastructure after the US District Court docket for the Japanese District of Virginia granted an order following a grievance filed on December 2 (the record of seized domains is out there right here).
In response to the court docket’s order (which additionally accommodates the record of seized websites), the domains had been redirected “to safe servers by altering the authoritative title servers to NS104a.microsoftintemetsafety.internet and NS104b.microsoftintemetsafety.internet.”
Microsoft’s Digital Crimes Unit (DCU) first noticed the risk group behind these malicious domains in 2016. Mandiant tracks them as Ke3chang and says they have been lively since a minimum of 2010.
Since 2019, it was noticed focusing on authorities entities throughout Latin America and Europe by Microsoft’s Menace Intelligence Heart (MSTIC) and Digital Safety Unit (DSU).
Nickel’s finish purpose is to deploy malware on compromised servers which allows its operators to watch their victims’ exercise, in addition to accumulate information and exfiltrate it to servers below their management.
These Chinese language-backed hackers use compromised third-party VPN (digital personal community) suppliers, credentials stolen in spear-phishing campaigns, and exploits focusing on unpatched on-premises Alternate Server and SharePoint servers to hack into their targets’ networks.
Extra data on the hacking group’s malicious exercise and indicators of compromise together with domains used of their assaults might be discovered right here.
“To this point, in 24 lawsuits – 5 in opposition to nation-state actors – we’ve taken down greater than 10,000 malicious web sites utilized by cybercriminals and practically 600 websites utilized by nation-state actors,” Burt added.
“We’ve additionally efficiently blocked the registration of 600,000 websites to get forward of felony actors that deliberate to make use of them maliciously sooner or later.”
In March 2020, the corporate took management of the U.S.-based infrastructure the Necurs spam botnet used to distribute malware payloads and infect tens of millions of computer systems.
In response to Microsoft, earlier than being taken down, Necurs despatched roughly 3.8 million spam messages to greater than 40.6 million targets over simply 58 days.
Redmond additionally sued the North Korean-linked Thallium cyber-espionage group in December 2019 and seized 50 domains a part of the hacking group’s malicious area infrastructure.
Microsoft’s Digital Crimes Unit additionally disrupted the Iran-backed APT35 (aka Charming Kitten, Phosphorus, or Ajax Safety Crew) risk actor in December 2019 after taking up servers utilized in its cyber assaults.
Beforehand, Microsoft filed 15 related instances in opposition to the Russian-backed group Strontium (aka Fancy Bear or APT28) in August 2018, which led to the seizure of 91 malicious domains.














