[ad_1]
The politically motivated Moses Workers hacker group has been noticed utilizing a customized multi-component toolset with the purpose of finishing up espionage in opposition to its targets as a part of a brand new marketing campaign that solely singles out Israeli organizations.
First publicly documented in late 2021, Moses Workers is believed to be sponsored by the Iranian authorities, with assaults reported in opposition to entities in Israel, Italy, India, Germany, Chile, Turkey, the U.A.E., and the U.S.
Earlier this month, the hacker collective was noticed incorporating a beforehand undocumented distant entry trojan (RAT) referred to as “StrifeWater” that masquerades because the Home windows Calculator app to evade detection.
“Shut examination reveals that the group has been lively for over a 12 months, a lot sooner than the group’s first official public publicity, managing to remain underneath the radar with a particularly low detection fee,” findings from FortiGuard Labs present.
The newest menace exercise includes an assault path that leverages the ProxyShell vulnerability in Microsoft Trade servers as an preliminary an infection vector to deploy two net shells, adopted by exfiltrating Outlook Information Recordsdata (.PST) from the compromised server.
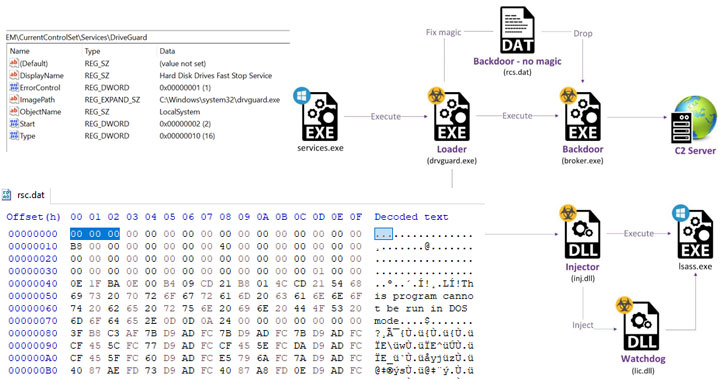
Subsequent phases of the an infection chain contain an try to steal credentials by dumping the reminiscence contents of a vital Home windows course of referred to as Native Safety Authority Subsystem Service (Lsass.exe), earlier than dropping and loading the “StrifeWater” backdoor (dealer.exe).
The set up of the “Dealer” implant, which is used to execute instructions fetched from a distant server, obtain recordsdata, and exfiltrate information from goal networks, is facilitated by a loader that masquerades as a “Arduous Disk Drives Quick Cease Service” dubbed “DriveGuard” (drvguard.exe).
On prime of that, the loader can also be chargeable for launching a watchdog mechanism (“lic.dll”) that ensures its personal service is rarely interrupted by restarting the DriveGuard each time it is stopped in addition to guaranteeing that the loader is configured to run routinely on system startup.
The dealer backdoor, for its half, can also be outfitted to delete itself from the disk utilizing a CMD command, seize screenshots, and replace the malware to switch the present module on the system with a file acquired from the server.
StrifeWater can also be notable for its makes an attempt to slide previous protection gateways by posing because the Home windows Calculator app (calc.exe), with FortiGuard Labs researchers discovering two older samples relationship again to the top of December 2020, suggesting that the marketing campaign has been operational for over a 12 months.
The attribution to Moses Workers is predicated on similarities within the net shells utilized in beforehand disclosed assaults and its sample of victimology.
“The group is extremely motivated, succesful, and set on damaging Israeli entities,” the researchers stated. “At this level, they proceed to rely upon 1-day exploits for his or her preliminary intrusion part. Though the assaults we recognized had been carried out for espionage functions, this doesn’t negate the likelihood that the operators will later flip to harmful measures.”
[ad_2]