[ad_1]

Researchers have discovered over 20,000 cases of publicly uncovered information heart infrastructure administration (DCIM) software program that monitor gadgets, HVAC management methods, and energy distribution items, which may very well be used for a spread of catastrophic assaults.
Information facilities home pricey methods that help enterprise storage options, operational methods, web site internet hosting, information processing, and extra.
The buildings that host information facilities should adjust to strict security laws regarding fireplace safety, airflow, electrical energy, and bodily safety.
Years of pursuing operational effectivity have launched “lights-out” information facilities, that are absolutely automated amenities managed remotely and usually function with out employees.
Nevertheless, the configuration of those methods is not all the time appropriate. Consequently, whereas the servers themselves could also be adequately protected against bodily entry, the methods that guarantee bodily safety and optimum efficiency generally aren’t.
A number of instances of unprotected methods
Investigators at Cyble have discovered over 20,000 cases of publicly uncovered DCIM methods, together with thermal and cooling administration dashboards, humidity controllers, UPS controllers, rack displays, and switch switches.
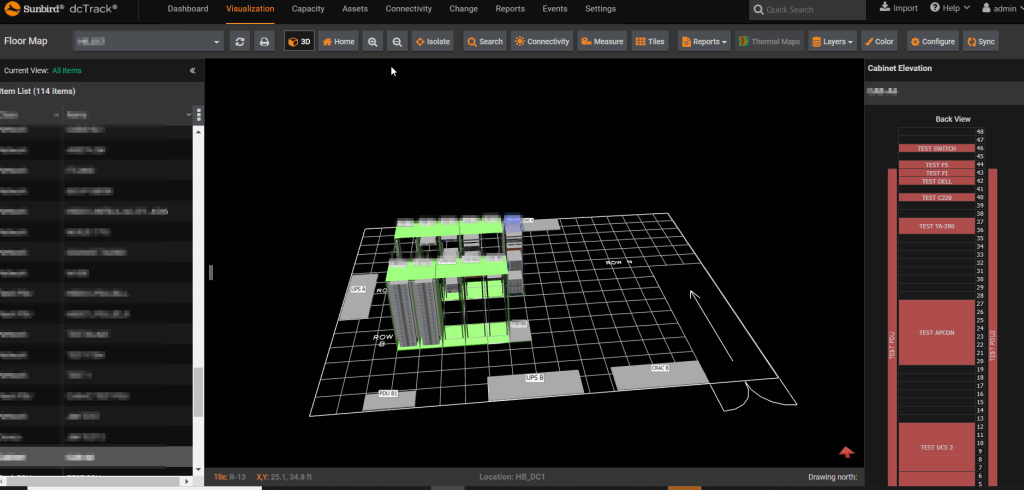
Supply: Cyble
Moreover, the analysts have been in a position to extract passwords from dashboards which they then used to entry precise database cases saved on the information heart.
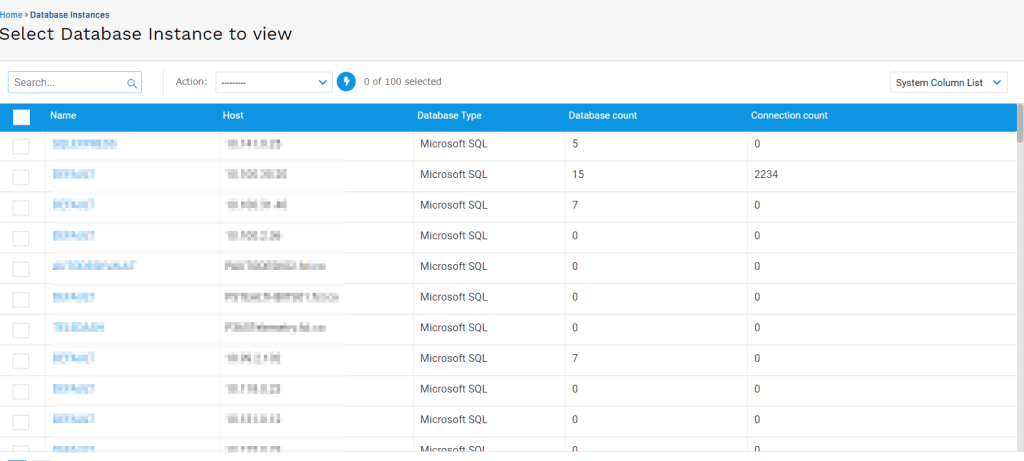
Supply: Cyble
The functions discovered by Cyble give full distant entry to information heart property, present standing experiences, and provide customers the capability to configure varied system parameters.
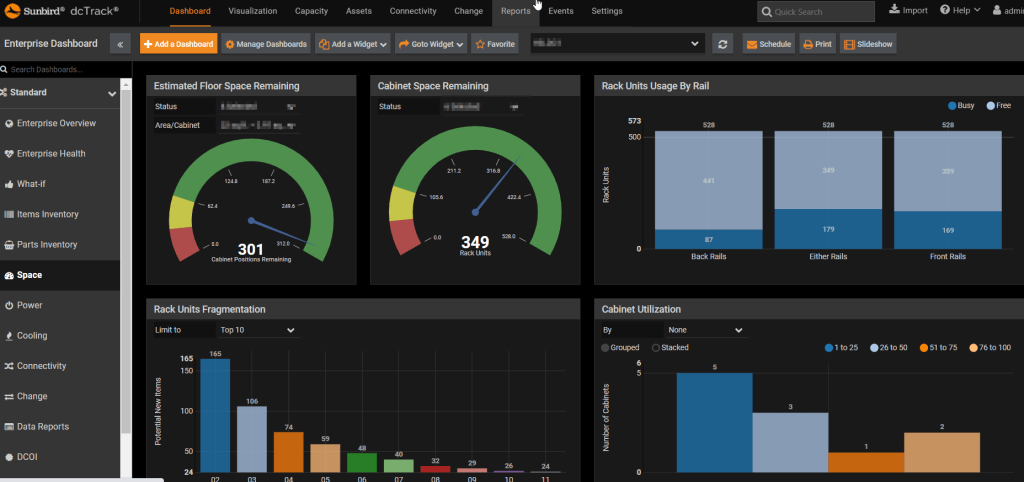
Supply: Cyble
Typically, the functions used default passwords or have been severely outdated, permitting risk actors to compromise them or override safety layers pretty simply.
Supply: Cyble
Potential influence
Exposing these methods with out enough safety signifies that anybody might change the temperature and humidity thresholds, configure voltage parameters to harmful ranges, deactivate cooling items, flip consoles off, put UPS gadgets to sleep, create false alarms, or change backup time intervals.
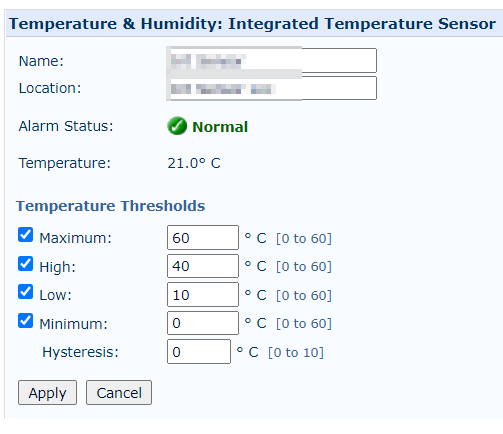
Supply: Cyble
These are all probably harmful acts which will end in bodily injury, information loss, system destruction, and a major financial influence on the focused organizations and their purchasers.
An instance of it is a fireplace incident within the Strasbourg-based OVH information heart in March 2021, attributable to a failure in one of many constructing’s UPS (uninterruptible energy provide) items.
Whereas that incidence wasn’t the results of hacking, it illustrates the magnitude of the injury that such assaults could cause to service suppliers and their prospects.
The hearth consumed hundreds of servers, irreversibly wiped information, and brought about service disruption to gaming servers, cryptocurrency exchanges, telecommunication corporations, information shops, and extra.
Even when no bodily hurt is finished, adversaries can use their entry to DCIM methods to exfiltrate information or lock the actual admins out and finally extort the information heart proprietor.
The implications, in any case, are dire, and shutting these loopholes ought to be a precedence. On that entrance, Cyble has knowledgeable the CERTs on every nation the place the uncovered methods have been positioned.
Over 20,000 ILO interfaces uncovered as effectively
Along with uncovered DCIM cases, safety researcher and ISC Handler Jan Kopriva discovered over 20,000 servers with uncovered ILO administration interfaces.
HPE Built-in Lights-Out (iLO) administration interfaces are used to supply distant low-level entry to a server, permitting directors to remotely energy off, energy on, reboot, and handle servers as in the event that they have been bodily in entrance of them.
Nevertheless, if not accurately secured, risk actors will now have full entry to servers at a pre-boot stage, permitting them to switch the working system and even {hardware} settings.
Like DCIM interfaces, it’s essential to safe ILO interfaces correctly and never expose them on to the Web to guard them from distant exploitation of vulnerabilities and password brute drive assaults.
[ad_2]