[ad_1]

A simulated phishing assault towards greater than 82,000 staff discovered that e-mails with a private impression resulted in additional clicks and that technical groups — reminiscent of IT staff and DevOps groups — clicked simply as typically and reported suspected phishing assaults much less typically in contrast with nontechnical groups
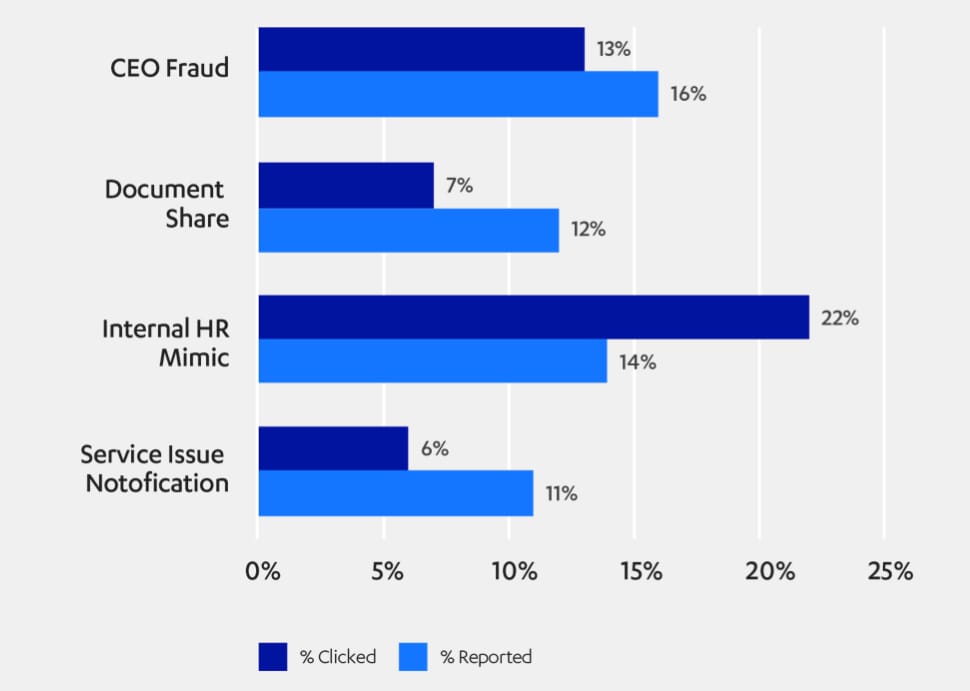
Software program-security agency F-Safe labored with 4 multinational organizations to create campaigns that includes one among 4 totally different phishing e-mails: a purported message from human sources, a pretend CEO fraud message, a spoofed document-sharing message, and a pretend discover of a service failure. On common, 12% of customers clicked on the phishing e-mail of their inboxes, however the price depended considerably on the content material.
As well as, the median time to report a suspected phishing assault was half-hour — good however considerably problematic as 1 / 4 of those that clicked on a phishing e-mail did so within the first 5 minutes, says Matthew Connor, F-Safe’s service supply supervisor and lead writer of the research report.
“The identification of an assault and a profitable phish is by far an important half right here,” he says. “It’s all nicely and good to coach your workers so they do not click on on an e-mail, but when the e-mails that do get by way of your community and to the inboxes, when you your self have not picked that up, that you must know that somebody goes to report that.
Quick Phish Reporting Is Key
The lesson is probably the the research‘s most essential: Velocity is important, Connor says. A technique to enhance the reporting price, and the pace, is to make reporting quite simple, reminiscent of a click on of a button. Two corporations that didn’t have such a simple option to report suspect phishing assaults had a mean reporting price of lower than 15%, whereas a 3rd firm that did have a ubiquitous button had a forty five% reporting price.
As a result of corporations must depend on staff to report phishing as quickly as attainable, maintaining the method as friction-free as attainable is essential, stated Riaan Naude, director of consulting at F-Safe, in a press release saying the outcomes.
“The proof within the research clearly factors to quick, painless reporting processes as frequent floor the place safety personnel and different groups can work collectively to enhance a company’s resilience towards phishing,” he says. “Getting this proper signifies that an assault could be detected and prevented earlier, as safety groups could solely have just a few valuable minutes to mitigate a possible compromise.”
The research additionally discovered that working in IT or DevOps didn’t equate to higher judgment when evaluating potential phishing assaults. Within the two organizations that had staff in IT or DevOps, each teams clicked check emails with equal — or better — probability than different departments of their organizations, F-Safe said within the report.
In a single group, 26% of DevOps crew members and 24% of IT crew members clicked on the check phishing payload, in contrast with 25% for the group general, whereas 30% from DevOps and 21% from IT clicked on the phishing payload within the second group, in contrast with 11% general.
The outcomes seemingly present the distinction between these staff who’ve been educated in IT safety and people who have a suspicious nature that enhances a place in IT safety.
“Phishing will get lumped into the class of information-security issues — and it’s — however it’s also only a vessel for a rip-off,” Connor says. “It’s simply the identical as having one thing snatched from you when you find yourself trying elsewhere. And there’s a mentality to defending towards that.”
One Click on
Whether or not this phishing research is a real illustration of the workforce’s state of vulnerability is debatable. The research measured solely two outcomes, with a single click on decided to be a profitable assault. Usually a phishing assault would require a number of steps as a part of its assault chain: The consumer clicks on an attachment or hyperlink within the e-mail after which permits a program to run or enters in info on a web site that appears respectable however is underneath attacker management.
Usually, the consumer will assume twice earlier than coming into of their info to a web site or clicking on the OK button to permit a program to run.
Nevertheless, F-Safe additionally needed to make concessions in establishing the e-mail lures. The principles of the simulation didn’t enable the corporate to tailor e-mail content material to lessons of customers, as an alternative requiring the messages be broadly relevant. As well as, the e-mail messages couldn’t embrace a emblem or use languages apart from English. Extra customization would seemingly have led to extra profitable assaults, F-Safe said within the report.
For instance, the document-sharing and repair situation notification emails weren’t branded as a widely known service, and that seemingly affected their click on price, the corporate argued, including that “[s]ecurity groups ought to be conscious that an actual attacker would possibly mimic a widely known service and have extra success.”
[ad_2]