[ad_1]
An preliminary entry dealer group tracked as Prophet Spider has been linked to a set of malicious actions that exploits the Log4Shell vulnerability in unpatched VMware Horizon Servers.
Based on new analysis revealed by BlackBerry Analysis & Intelligence and Incident Response (IR) groups right this moment, the cybercrime actor has been opportunistically weaponizing the shortcoming to obtain a second-stage payload onto the victimized techniques.
The payloads noticed embody cryptocurrency miners, Cobalt Strike Beacons, and internet shells, corroborating a earlier advisory from the U.Okay. Nationwide Well being Service (NHS) that sounded the alarm on energetic exploitation of the vulnerabilities in VMware Horizon servers to drop malicious internet shells and set up persistence on affected networks for follow-on assaults.
Log4Shell is a moniker used to seek advice from an exploit affecting the favored Apache Log4j library that leads to distant code execution by logging a specifically crafted string. Since public disclosure of the flaw final month, menace actors have been fast to operationalize this new assault vector for quite a lot of intrusion campaigns to achieve full management of affected servers.
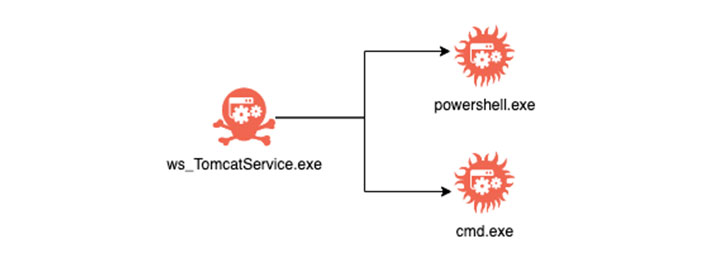
BlackBerry mentioned it noticed situations of exploitation mirroring techniques, methods, and procedures (TTPs) beforehand attributed to the Prophet Spider eCrime cartel, together with using “C:WindowsTemp7fde” folder path to retailer malicious information and “wget.bin” executable to fetch further binaries in addition to overlaps in infrastructure utilized by the group.
“Prophet Spider primarily features entry to victims by compromising weak internet servers, and makes use of quite a lot of low-prevalence instruments to attain operational targets,” CrowdStrike famous in August 2021, when the group was noticed actively exploiting flaws in Oracle WebLogic servers to achieve preliminary entry to focus on environments.
Like with many different preliminary entry brokers, the footholds are bought to the best bidder on underground boards positioned at midnight internet, who then exploit the entry for ransomware deployment. Prophet Spider is thought to be energetic since not less than Could 2017.
That is removed from the primary time internet-facing techniques operating VMware Horizon have come underneath assault utilizing Log4Shell exploits. Earlier this month, Microsoft known as out a China-based operator tracked as DEV-0401 for deploying a brand new ransomware pressure known as NightSky on the compromised servers.
The onslaught in opposition to Horizon servers has additionally prompted VMware to induce its clients to apply the patches instantly. “The ramifications of this vulnerability are critical for any system, particularly ones that settle for visitors from the open Web,” the virtualization providers supplier cautioned.
“When an entry dealer group takes curiosity in a vulnerability whose scope is so unknown, it is a good indication that attackers see vital worth in its exploitation,” Tony Lee, vice chairman of world providers technical operations at BlackBerry, mentioned.
“It is possible that we are going to proceed to see felony teams exploring the alternatives of the Log4Shell vulnerability, so it is an assault vector in opposition to which defenders must train fixed vigilance,” Lee added.
.
[ad_2]