[ad_1]

EXCLUSIVE: Hackers related to the Russian Federation International Intelligence Service (SVR) continued their incursions on networks of a number of organizations after the SolarWinds supply-chain compromise utilizing two lately found refined threats.
The malicious implants are a variant of the GoldMax backdoor for Linux methods and a totally new malware household that cybersecurity firm CrowdStrike now tracks as TrailBlazer.
Each threats have been utilized in StellarParticle campaigns since a minimum of mid-2019 however had been recognized solely two years later, throughout incident response investigations.
StellarParticle assaults have been attributed to the APT29 hacking group has been operating cyber espionage campaigns for greater than 12 years and is also referred to as CozyBear, The Dukes, and Yttrium.
Stealing cookies for MFA bypass
In a report shared solely with BleepingComputer, cybersecurity firm CrowdStrike at present describes intimately the most recent ways, methods, and procedures (TTPs) noticed in cyberattacks from the Cozy Bear state-sponsored hackers.
Whereas among the methods are considerably widespread at present, Cozy Bear has been utilizing them lengthy earlier than they grew to become standard:
- credential hopping
- hijacking Workplace 365 (O365) Service Principal and Software
- bypassing multi-factor authentication (MFA) by stealing browser cookies
- stealing credentials utilizing Get-ADReplAccount
Credential hopping was the primary stage of the assault, permitting the risk actor to log into Workplace 365 from an inside server that the hackers reached by a compromised public-facing system.
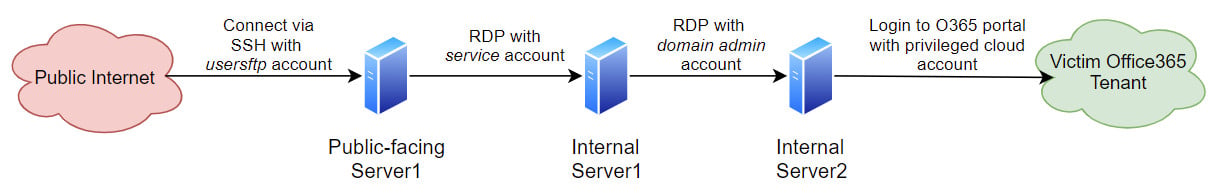
CrowdStrike says that this method is tough to identify on environments with little visibility into identification utilization since hackers may use multiple area administrator account.
Bypassing MFA to entry cloud assets by stealing browser cookies has been used since earlier than 2020. CrowdStrike says that APT29 stored a low profile after decrypting the authentication cookies, possible offline, through the use of the Cookie Editor extension for Chrome to replay them; they deleted the extension afterwards.
“This extension permitted bypassing MFA necessities, because the cookies, replayed by the Cookie Editor extension, allowed the risk actor to hijack the already MFA-approved session of a focused person” – CrowdStrike
This allowed them to maneuver laterally on the community and attain the following stage of the assault, connecting to the sufferer’s O365 tenant for the following stage of the assault.
CrowdStrike’s report describes the steps that APT29 took to attain persistence ready that allowed them to learn any e mail and SharePoint or OneDrive recordsdata of the compromised group.
GoldMax for Linux and TrailBlazer
Throughout their incident response work on APT29 StellarParticle assaults, CrowdStrike’s researchers used the Consumer Entry Logging (UAL) database to determine earlier malicious account utilization, which led to discovering the GoldMax for Linux and TrailBlazer malware.
CrowdStrike says that TrailBlazer is a totally new malware household, whereas GoldMax for Linux backdoor “is sort of equivalent in performance and implementation to the beforehand recognized Might 2020 Home windows variant.”
The researchers imagine that the little variations are between the 2 GoldMax variations are as a result of steady enhancements from the developer for long-term detection evasion.
GoldMax was possible used for persistence (a crontab with a “@reboot” line for a non-root person) over lengthy durations in StellarParticle campaigns. The backdoor stayed undetected by posing as a respectable file in a hidden listing.
The TrailBlazer implant additionally hid beneath the title of a respectable file and it was configured for persistence utilizing the Home windows Administration Instrumentation (WMI) Occasion Subscriptions, a comparatively new method in 2019, the earliest recognized date for its deployment on sufferer methods.
TrailBlazer managed to maintain communication with the command and management (C2) server covert by masking it as respectable Google Notifications HTTP requests.
CrowdStrike notes that the implant has modular performance and “a really low prevalence” and that it shares similarities with different malware households utilized by the identical risk actor, equivalent to GoldMax and Sunburst (each used within the SolarWinds supply-chain assault).
Tim Parisi, Director of Skilled Companies at CrowdStrike, instructed BleepingComputer that the covert exercise of the 2 malware items delayed the invention of the 2 malware items, because the researchers discovered them in mid-2021.
Recon and transferring to Workplace 365
After getting access to a goal group’s infrastructure and established persistence, APT29 hackers took each alternative to gather intelligence that might enable them to additional the assault.
One fixed tactic was to attract info from the sufferer’s inside data repositories, the so-called wikis. These paperwork can maintain delicate particulars particular to numerous providers and merchandise within the group.
“This info included objects equivalent to product/service structure and design paperwork, vulnerabilities and step-by-step directions to carry out numerous duties. Moreover, the risk actor considered pages associated to inside enterprise operations equivalent to improvement schedules and factors of contact. In some cases these factors of contact had been subsequently focused for additional information assortment” – CrowdStrike
Parisi instructed us that accessing firm wikis was a typical APT29 reconnaissance exercise within the investigated StellarParticle assaults.
CrowdStrike’s deep dive into APT29’s StellarParticle campaigns provides particulars on how the risk actor related to the sufferer’s O365 tenant by the Home windows Azure Energetic Listing PowerShell Module, and carried out enumeration queries for roles, members, customers, domains, accounts, or a service principal’s credentials.
When analyzing the log entries, the researchers seen that the risk actor additionally executed the AddServicePrincipalCredentials command.
“CrowdStrike analyzed the configuration settings within the sufferer’s O365 tenant and found {that a} new secret had been added to a built-in Microsoft Azure AD Enterprise Software, Microsoft StaffHub Service Principal, which had Software degree permissions” – CrowdSrike
The adversary had added a brand new secret to the appliance and set its validity for greater than 10 years, the researchers notice.
The permission degree obtained this manner let hackers entry to all mail and SharePoint/OneDrive recordsdata within the firm and allowed them to “new accounts and assign administrator privileges to any account within the group.”
Sustaining persistence
As soon as Cozy Bear/APT29 established persistence in a goal group they might preserve it for so long as potential, generally helped by the poor safety hygiene of the compromised group.
The longest time the risk actor spent inside a company was two years, Parisi instructed BleepingComputer. Persisting this lengthy wouldn’t be potential with out some effort from the hackers, since organizations usually rotate credentials as a safety precaution.
To stop dropping entry, Cozy Bear hackers would periodically refresh the stolen credentials by stealing new ones, oftentimes by way of Mimikatz.
In a minimum of one case, although, the directors of the compromised firm reset their passwords to the identical ones, thus defeating the aim of credential rotation.
Cozy Bear hackers are among the most refined risk actors within the cyber espionage world, with high abilities to infiltrate and keep undetected on an organization’s infrastructure for lengthy durations.
In the course of the StellarParticle assaults they demonstrated knowledgeable data in Azure, Workplace 365, and Energetic Listing administration.
[ad_2]
![Tax scams, carder busts and crypto capers [Podcast + Transcript] – Bare Safety Tax scams, carder busts and crypto capers [Podcast + Transcript] – Bare Safety](https://nakedsecurity.sophos.com/wp-content/uploads/sites/2/2021/09/ns-1200-logo-podcast-with-mic.png?w=775)

