[ad_1]
In an indication that risk actors constantly shift ways and replace their defensive measures, the operators of the SolarMarker data stealer and backdoor have been discovered leveraging stealthy tips to ascertain long-term persistence on compromised programs.
Cybersecurity agency Sophos, which noticed the brand new habits, stated that the distant entry implants are nonetheless being detected on focused networks regardless of the marketing campaign witnessing a decline in November 2021.
Boasting of data harvesting and backdoor capabilities, the .NET-based malware has been linked to at the very least three totally different assault waves in 2021. The primary set, reported in April, took benefit of search engine poisoning strategies to trick enterprise professionals into visiting sketchy Google websites that put in SolarMarker on the sufferer’s machines.
Then in August, the malware was noticed concentrating on healthcare and schooling sectors with the purpose of gathering credentials and delicate data. Subsequent an infection chains documented by Morphisec in September 2021 highlighted the usage of MSI installers to make sure the supply of the malware.
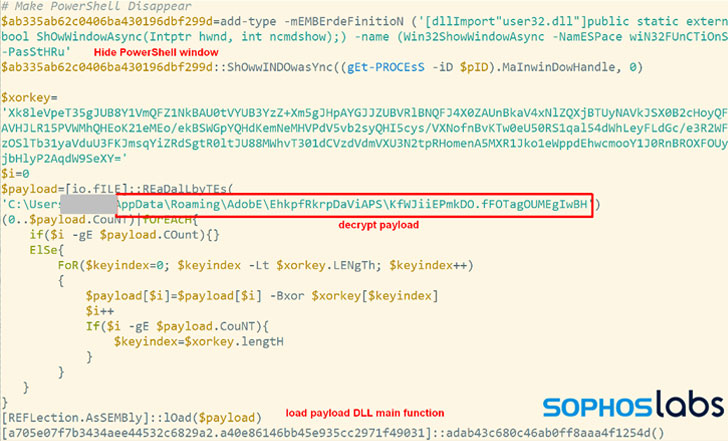
The SolarMarker modus operandi commences with redirecting victims to decoy websites that drop the MSI installer payloads, which, whereas executing seemingly authentic set up applications comparable to Adobe Acrobat Professional DC, Wondershare PDFelement or Nitro Professional, additionally launches a PowerShell script to deploy the malware.
“These search engine optimisation efforts, which leveraged a mix of Google Teams discussions and misleading net pages and PDF paperwork hosted on compromised (often WordPress) web sites, have been so efficient that the SolarMarker lures have been often at or close to the highest of search outcomes for phrases the SolarMarker actors focused,” Sophos researchers Gabor Szappanos and Sean Gallagher stated in a report shared with The Hacker Information.
The PowerShell installer is designed to change the Home windows Registry and drop a .LNK file into Home windows’ startup listing to ascertain persistence. This unauthorized change leads to the malware getting loaded from an encrypted payload hidden amongst what the researchers known as a “smokescreen” of 100 to 300 junk recordsdata created particularly for this function.
“Usually, one would anticipate this linked file to be an executable or script file,” the researchers detailed. “However for these SolarMarker campaigns the linked file is among the random junk recordsdata, and can’t be executed itself.
What’s extra, the distinctive and random file extension used for the linked junk file is utilized to create a customized file sort key, which is finally employed to execute the malware throughout system startup by operating a PowerShell command from the Registry.
The backdoor, for its half, is ever-evolving, that includes an array of functionalities that permit it to steal data from net browsers, facilitate cryptocurrency theft, and execute arbitrary instructions and binaries, the outcomes of that are exfiltrated again to a distant server.
“One other essential takeaway […], which was additionally seen within the ProxyLogon vulnerabilities concentrating on Trade servers, is that defenders ought to all the time verify whether or not attackers have left one thing behind within the community that they’ll return to later,” Gallagher stated. “For ProxyLogon this was net shells, for SolarMarker this can be a stealthy and chronic backdoor that in accordance with Sophos telematics remains to be lively months after the marketing campaign ended.”
[ad_2]