[ad_1]
Tales from the SOC is a weblog collection that describes latest real-world safety incident investigations performed and reported by the AT&T SOC analyst workforce for AT&T Managed Menace Detection and Response clients.
Govt abstract
WannaCry malware was first found in Could 2017 and a patch was launched roughly two months previous to its public launch. Nonetheless, 230,000 computer systems have been globally affected by WannaCry as of three/31/2021. It’s unlucky to listen to, however many corporations stay weak to this assault on account of unpatched techniques. We frequently see that by the point some corporations replace their techniques, they’ve already skilled a breach.
The Managed Menace Detection and Response (MTDR) SOC analyst workforce acquired 56 alarms associated to the suspicious use of port 445 inside a 24-hour timeframe. Given the excessive inflow of alarms, our workforce created an Investigation to disclose which belongings have been utilizing port 445, the locations that have been being communicated with, and the frequency of the connections. The shopper shortly recognized that the supply belongings have been unpatched Home windows 7 manufacturing servers affected by WannaCry. They have been in a position to phase the contaminated computer systems, block SMB port 445, use Pattern Micro’s Anti-Menace Toolkit to scrub the machines, after which return the belongings to the community.
Investigation
Preliminary alarm assessment
Indicators of compromise (IOC)
The preliminary alarms that triggered this investigation have been created from a customized alarm. The MTDR workforce can create customized alarms particular to the shoppers surroundings to assist enhance time to response. The alarms have been triggered when occasions from Pattern Micro confirmed belongings utilizing Server Message Block (SMB) port 445 during which a single supply was speaking with a number of locations.
This preliminary alarm was considered one of many who was generated. The alarms got here in with a precedence of “Low” as a result of use of SMB port 445 is widespread throughout the buyer’s group. Our workforce and the shopper started to suspect {that a} breach had occurred as a result of excessive quantity of inside connections in addition to these connections trying to achieve exterior IP’s.
Expanded investigation
Occasions search
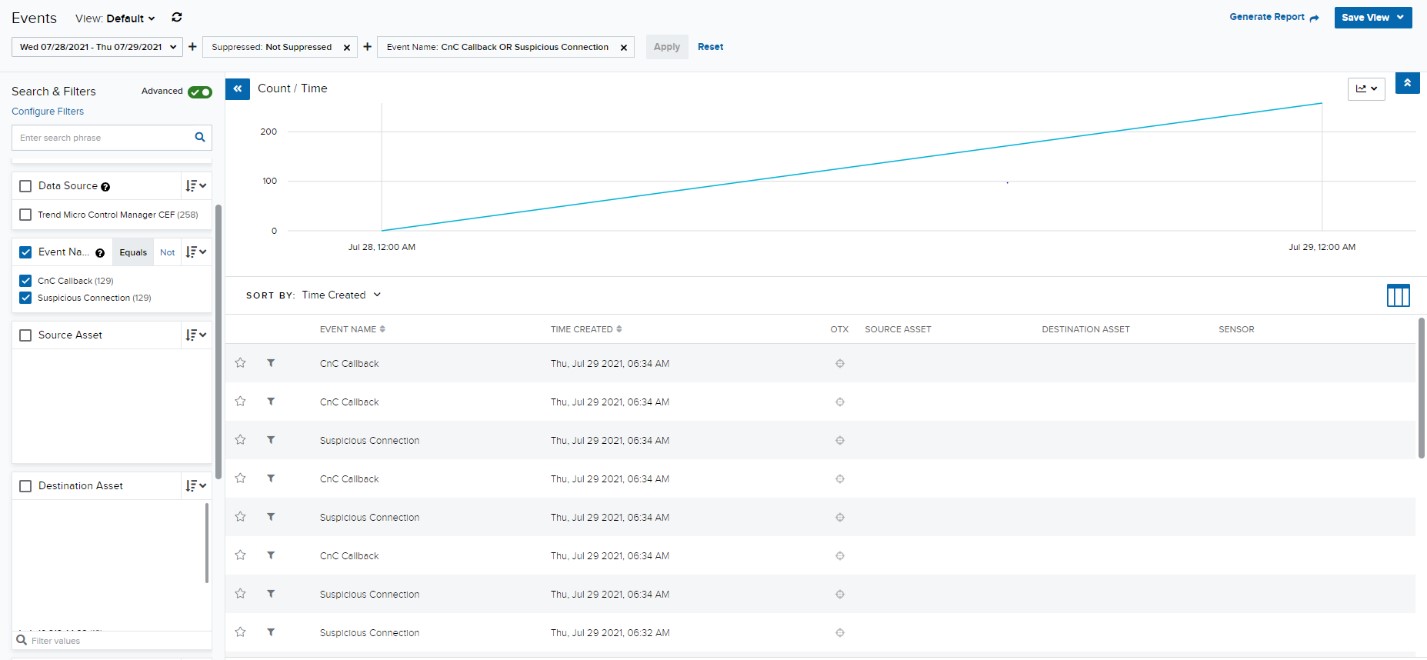
Upon additional investigation, we looked for occasions “CnC Callback” and “Suspicious Connection”. The workforce then analyzed these occasions over a 24-hour interval. This evaluation revealed the entire inside belongings and their occasions’ sources and locations. These belongings have been speaking over port 445 and have been doubtless compromised techniques.
Occasion deep dive
Persevering with with the investigation, we realized that the affected belongings have been speaking with unknown exterior IP’s. Many of those outbound connections have been blocked on the firewall; nonetheless, at this level, we have been in a position to pivot from the exterior IP’s to search for extra affected belongings.
Reviewing for extra indicators
We then made a whole checklist of all probably affected inside belongings. After individually inspecting the belongings, we found the next occasion: “Ransom_WCRY.SM2” on a number of of the belongings. This specific occasion confirmed our suspicion that this was, certainly, the WannaCry malware.
Response
Constructing the investigation
Inside minutes of the workforce creating the investigation, the shopper escalated the case. The shopper seen that the entire related belongings have been a part of a single subnet remoted to at least one sector of their enterprise. The shopper then remoted the subnet of probably affected belongings from the remainder of the community to be able to start reviewing the machines.
Whereas the belongings have been being scanned for additional indicators of compromise, we concerned the shopper’s Menace Hunter (TH). The TH helped generate extra studies of all inside belongings that have been related to the malicious occasions.
At this level, the shopper blocked port 445 on the belongings, used Pattern Micro’s Anti-Menace Toolkit to scrub the machines, after which returned the belongings to the community.
We continued to intently monitor the shopper’s community for additional indicators of compromise from the WannaCry malware. We maintained this vigilance till the workforce ensured the scenario had been absolutely resolved.
Buyer interplay
Our workforce labored intently with the shopper to make sure we have been updated with any adjustments being made to their techniques. Due to the shut communication between our workforce and the shopper, we have been in a position to shortly assess the scenario, examine acceptable belongings, and resolve the problem earlier than any techniques could possibly be encrypted for ransomware.
[ad_2]