[ad_1]
This weblog was written by an impartial visitor blogger.
Formidable info safety specialists function a important a part of cyber danger administration.
The company is accountable for structuring IT and data safety actions to guard its knowledge sources, corresponding to {hardware}, software program, and procedures.
To remain aggressive, enterprises should design and set up safe environments that retain confidentiality and privateness whereas additionally guaranteeing the integrity of company info. This may be achieved by means of the usage of cyber danger administration approaches.
This text explores the necessity for safety and supplies an summary of cyber danger evaluation. We’ll talk about management categorization and approaches with an instance.
Want for safety
Organizations have lengthy encountered varied varieties of danger. Nonetheless, cyber danger has emerged as a important part – evaluating dangers to firms, their info, and their monetary outcomes is a precedence.
Malicious hackers are making the most of technological developments and developments to hack and exploit the sources of companies.
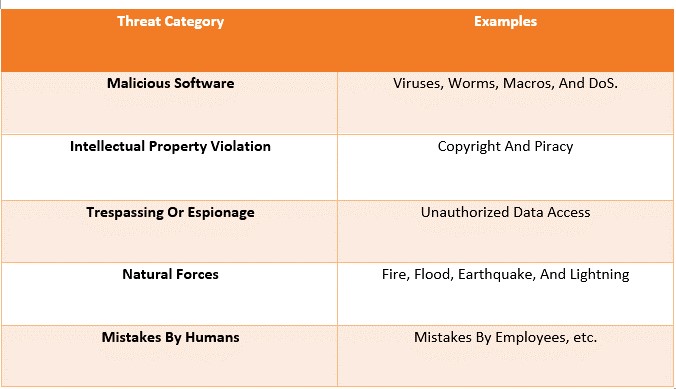
The next desk reveals some classifications that mirror real looking and outstanding threats to an organization’s personnel, knowledge, and know-how.
Every group should prioritize the dangers it confronts relying on the safety situation in which it really works, its organizational danger strategy, and the vulnerability ranges at which its sources execute.
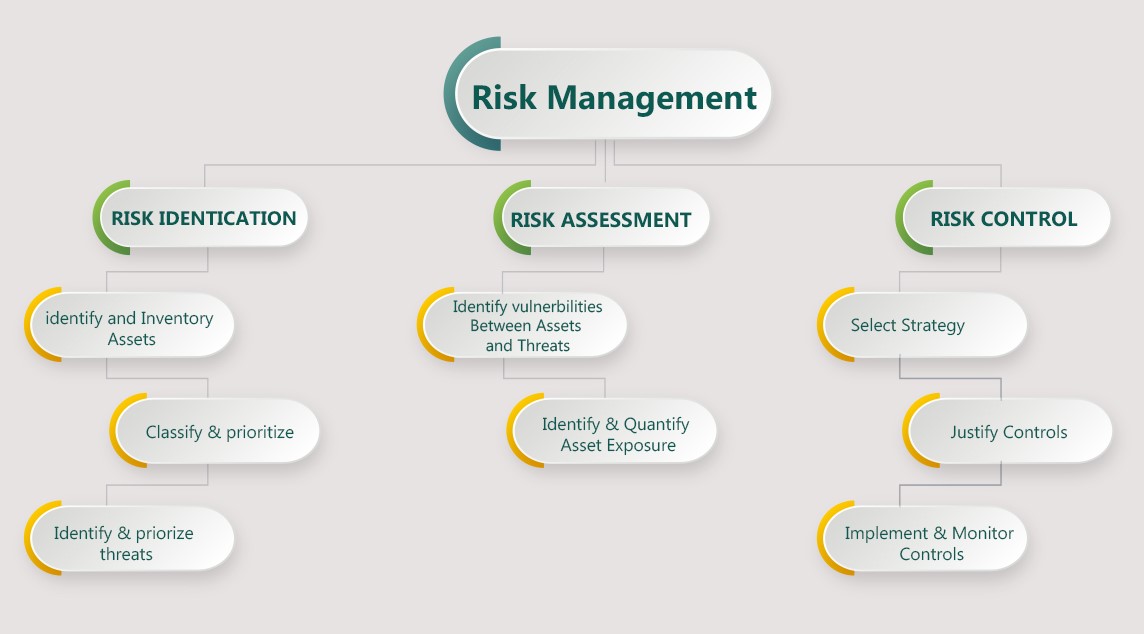
Cyber danger administration
Threat administration is the strategy of figuring out vulnerabilities to an organization’s knowledge sources and structure and implementing methods to cut back that danger to tolerable ranges.
The three main steps of cyber danger administration are:
- Threat identification
- Threat evaluation
- Threat management
Cyber danger evaluation instance
Let’s perceive the phases of danger evaluation with the assistance of an instance.
For example, your division head assigns you to carry out danger administration and shares the community structure, worker lists, software program listing, and many others., with you.
Threat identification
Step one of identification is to determine the belongings, categorize, prioritize and retailer them within the stock.
It’s easy to determine quite a few belongings first by glancing at community structure, however preserving them collectively in reminiscence is tough, so why not categorize the belongings with the parts of data safety administration.
|
Conventional Elements |
SecSDLC Elements |
Examples |
|
Individuals |
Staff |
|
|
|
Non-Staff |
|
|
Software program, {Hardware}, Community |
System Gadgets/Networking Elements |
|
|
Process |
Process |
|
|
Knowledge |
Data |
|
After figuring out and categorizing belongings, we have to create a list of all belongings.
- We should not prejudge the price of each asset when compiling a list of information belongings.
- Whether or not automated or handbook, the stock strategy wants vital planning.
- It should additionally embrace the sensitivity and safety degree of every merchandise within the stock.
After stock, we carry out relative assessments to ensure that we assign essentially the most vital belongings high precedence. It’s also possible to ask a number of inquiries to allocate weight to belongings for danger evaluation. Questions, corresponding to:
- What useful resource is related to the very best income margin?
- Which of the belongings is the most expensive to switch or to safeguard?
- Which asset’s elimination or corruption is likely to be essentially the most distressing or expose you to the best danger?
After performing preliminary identification, we begin an evaluation of the dangers affecting the corporate.
In the event you presume that each danger will certainly goal each asset, the challenge scope instantly grows so huge that planning turns into unattainable.
We must always assess every menace for its means to place the corporate in jeopardy. That is menace evaluation. Answering a couple of easy questions may help you begin a menace evaluation:
- What threats pose the best hazard to an organization’s belongings?
- How a lot will the assault value if knowledge restoration is required?
- Which threats pose excessive dangers to the info owned by an organization?
Threat evaluation
It’s possible you’ll assess the comparative danger for every vulnerability now that you have recognized the group’s belongings and threats. We seek advice from this as danger evaluation. Now, determine the vulnerability related to belongings and threats.
|
Property |
Threats |
Vulnerability |
|
Server |
|
|
|
Web sites |
|
|
|
Rogue Gadgets |
|
Every asset is given a danger degree or grade throughout danger evaluation. Whereas this quantity has no precise worth, it helps decide the relative danger related to each delicate asset.
There’s additionally a primary formulation we use to evaluate the danger.
Threat = chance of prevalence of vulnerability * worth of the knowledge asset – the share of danger mitigated by present controls + uncertainty of present data of the vulnerability.
Let’s make the most of this formulation with an instance.
Now we have an “asset A” with a price of 40 and one vulnerability with a likelihood of 1.0 with no safety controls. Your information are 80% credible*.
(If the reliability is 95%, the uncertainty is 5%.)
(40 × 1.0) – 0% + 5% = 45
So, the vulnerability of asset A ranks as 45.
You may most probably have listings of belongings with info by the tip of the danger evaluation. The purpose was to find belongings’ info with safety flaws and create a compilation of them, graded from most susceptible to least susceptible.
You gathered and saved a plethora of information in regards to the belongings, the dangers they pose, and the dangers they disclose whereas compiling this listing and so forth.
Threat management
After finishing the danger identification, and danger evaluation course of, we finish the danger administration with danger management.
Threat management give us 5 methods to cope with the dangers, and they’re:
- Defend
- Switch
- Mitigate
- Settle for
- Terminate
Let’s have a look at the under desk to be taught the management methods in depth.
|
Threat Management Methods |
Definition |
Examples |
|
Defend |
The defend technique tries to eradicate the vulnerability from being exploited. |
|
|
Switch |
Utilizing the switch management approach, we shift the dangers to different sources, actions, or corporations. |
|
|
Mitigate |
With planning and response, the mitigation management approach seeks to minimize the impact of vulnerability exploitation. |
|
|
Settle for |
The settle for management technique is doing much less to forestall a vulnerability from being exploited and accepting the results of such an assault. |
|
|
Terminate |
The corporate’s terminate management technique encourages it to eradicate industrial operations that pose unmanageable dangers.
|
|
Threat reporting
The final step we have now is danger reporting. It is a essential a part of danger evaluation. After performing the complete danger administration course of, it’s a must to doc it. Threat reviews are a way of informing those who have to know in regards to the challenge and firm’s dangers.
Conclusion
In a nutshell, as you progress alongside the danger administration course of, you may have a higher understanding of your company’s structure, your most essential knowledge, and how one can enhance your administration and safety.
[ad_2]