[ad_1]
In December 2021, researchers found a brand new ransomware-as-a-service named ALPHV (a.ok.a. “BlackCat“), thought of to be the primary skilled cybercrime group to create and use a ransomware pressure written within the Rust programming language. On this publish, we’ll discover a few of the clues left behind by a developer who was seemingly employed to code the ransomware variant.

Picture: Varonis.
In accordance with an evaluation launched this week by Varonis, ALPHV is actively recruiting operators from a number of ransomware organizations — together with REvil, BlackMatter and DarkSide — and is providing associates as much as 90 p.c of any ransom paid by a sufferer group.
“The group’s leak web site, lively since early December 2021, has named over twenty sufferer organizations as of late January 2022, although the whole variety of victims, together with people who have paid a ransom to keep away from publicity, is probably going larger,” Varonis’s Jason Hill wrote.
One concern about extra malware shifting to Rust is that it’s thought of a way more safe programming language in comparison with C and C++, writes Catalin Cimpanu for The Report. The upshot? Safety defenders are continually on the lookout for coding weaknesses in lots of ransomware strains, and if extra begin transferring to Rust it might turn into harder to search out these smooth spots.
Researchers at Recorded Future say they imagine the ALPHV/BlackCat writer was beforehand concerned with the notorious REvil ransomware cartel in some capability. Earlier this month the Russian authorities introduced that at america’ request it arrested 14 people in Russia regarded as REvil operators.
Nonetheless, REvil rolls on regardless of these actions, in response to Paul Roberts at ReversingLabs. “The current arrests have NOT led to a noticeable change in detections of REvil malicious recordsdata,” Roberts wrote. “In truth, detections of recordsdata and different software program modules related to the REvil ransomware elevated modestly within the week following the arrests by Russia’s FSB intelligence service.”
In the meantime, the U.S. State Division has a standing $10 million reward for data resulting in the identification or location of any people holding key management positions in REvil.
WHO IS BINRS?
A confidential supply just lately had a non-public dialog with a help consultant who fields questions and inquiries on a number of cybercrime boards on behalf of a giant and well-liked ransomware associates program. The affiliate rep confirmed {that a} coder for ALPHV was identified by the deal with “Binrs” on a number of Russian-language boards.
On the cybercrime discussion board RAMP, the consumer Binrs says they’re a Rust developer who’s been coding for six years. “My stack is Rust, nodejs, php, golang,” Binrs stated in an introductory publish, through which they declare to be fluent in English. Binrs then indicators the publish with their identification quantity for ToX, a peer-to-peer instantaneous messaging service.
That very same ToX ID was claimed by a consumer known as “smiseo” on the Russian discussion board BHF, through which smiseo advertises “clipper” malware written in Rust that swaps within the attacker’s bitcoin tackle when the sufferer copies a cryptocurrency tackle to their pc’s non permanent clipboard.
The nickname “YBCat” marketed that very same ToX ID on Carder[.]uk, the place this consumer claimed possession over the Telegram account @CookieDays, and stated they could possibly be employed to do software program and bot improvement “of any degree of complexity.” YBCat largely offered “installs,” providing paying clients to capability to load malware of their alternative on hundreds of hacked computer systems concurrently.
There may be additionally an lively consumer named Binrs on the Russian crime discussion board wwh-club[.]co who says they’re a Rust coder who may be reached on the @CookieDays Telegram account.
On the Russian discussion board Lolzteam, a member with the username “DuckerMan” makes use of the @CookieDays Telegram account in his signature. In a single thread, DuckerMan promotes an associates program known as CookieDays that lets folks become profitable by getting others to put in cryptomining applications which are contaminated with malware. In one other thread, DuckerMan is promoting a distinct clipboard hijacking program known as Chloe Clipper.

The CookieDays moneymaking program.
In accordance with risk intelligence agency Flashpoint, the Telegram consumer DuckerMan employed one other alias — Sergey Duck. These accounts had been most lively within the Telegram channels “Financial institution Accounts Promoting,” “Malware builders group,” and “Raidforums,” a well-liked English-language cybercrime discussion board.
I AM DUCKERMAN
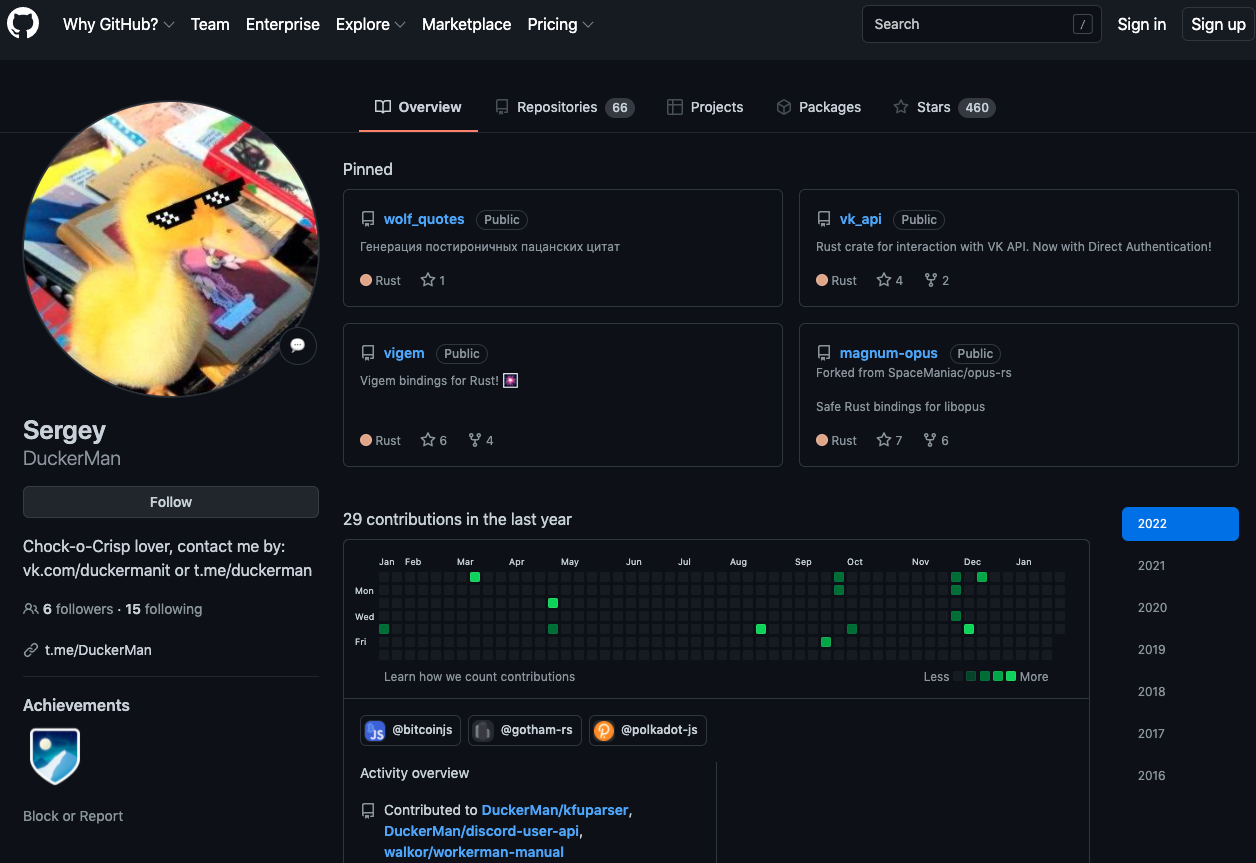
The GitHub account for a Sergey DuckerMan lists dozens of code repositories this consumer has posted on-line through the years. The vast majority of these initiatives had been written in Rust, and the remaining in PHP, Golang and Nodejs — the identical coding languages specified by Binrs on RAMP. The Sergey DuckerMan GitHub account additionally says it’s related to the “DuckerMan” account on Telegram.
Sergey DuckerMan has left many accolades for different programmers on GitHub — 460 to be precise. In June 2020, for instance, DuckerMan gave a star to a proof-of-concept ransomware pressure written in Rust.
Sergey DuckerMan’s Github profile says their social media account at Vkontakte (Russian model of Fb/Meta) is vk.com/duckermanit. That profile is restricted to friends-only, however states that it belongs to a Sergey Pechnikov from Shuya, Russia.
A have a look at the Duckermanit VKontakte profile in Archive.org exhibits that till just lately it bore a distinct title: Sergey Kryakov. The present profile picture on the Pechnikov account exhibits a younger man standing intently subsequent to a younger lady.
KrebsOnSecurity reached out to Pechnikov in transliterated Russian by way of the moment message function constructed into VKontakte.
“I’ve heard about ALPHV,” Pechnikov replied in English. “It sounds actually cool and I’m glad that Rust turns into increasingly well-liked, even in malware sphere. However I don’t have any connections with ransomware in any respect.”
I started explaining the clues that led to his VK account, and the way a key cybercriminal actor within the ransomware area had confirmed that Binrs was a core developer for the ALPHV ransomware.
“Binrs isn’t even a programmer,” Pechnikov interjected. “He/she will’t be a DuckerMan. I’m DuckerMan.”
BK: Proper. Nicely, in response to Flashpoint, the Telegram consumer DuckerMan additionally used the alias Sergey Duck.
Sergey: Yep, that’s me.
BK: So you may see already how I arrived at your profile?
Sergey: Yep, you’re a extremely good investigator.
BK: I observed this profile used to have a distinct title connected to it. A ‘Sergey Kryakov.’
Sergey: It was my outdated surname. However I hated it a lot I modified it.
BK: What did you imply Binrs isn’t even a programmer?
Sergey: I haven’t discovered any [of] his accounts on websites like GitHub/stack overflow. I’m unsure, does binrs promote Rust Clipper?
BK: So you recognize his work! I take it that regardless of all of this, you preserve you aren’t concerned in coding malware?
Sergey: Nicely, no, however I’ve some “connections” with these guys. Talking about Binrs, I’ve been researching his character since October too.
BK: Fascinating. What made you need to analysis his character? Additionally, please assist me perceive what you imply by “connections.”
Sergey: I feel he’s really a gaggle of some folks. I’ve written him on telegram from totally different accounts, and his method of talking is totally different. Perhaps a few of them someway tied with ALPHV. However on boards (I’ve checked solely XSS and Exploit) his methods of talking are the identical.
BK: …..
Sergey: I don’t know the right way to clarify this. By the best way, binrs now’s actually silent, I feel he’s mendacity low. Nicely, that is all I do know.
Little doubt he’s. I loved talking with Sergey, however I additionally had problem believing most of what he stated. Additionally, I used to be bothered that Sergey hadn’t precisely disputed the logic behind the clues that led to his VK account. In truth, he’d said a number of instances that he was impressed with the investigation.
In lots of earlier Breadcrumbs tales, it’s common at this level for the interviewee to assert they had been being arrange or framed. However Sergey by no means even floated the concept.
I requested Sergey what would possibly clarify all these connections if he wasn’t someway concerned in coding malicious software program. His reply, our last alternate, was once more equivocal.
“Nicely, all I’ve is code on my github,” he replied. “So it may be used [by] anybody, however I don’t assume my initiatives go well with for malwares.”
[ad_2]