[ad_1]
Researchers from the Bitdefender Cellular Threats crew mentioned they’ve intercepted greater than 100,000 malicious SMS messages making an attempt to distribute Flubot malware for the reason that starting of December.
“Findings point out attackers are modifying their topic strains and utilizing older but confirmed scams to entice customers to click on,” the Romanian cybersecurity agency detailed in a report printed Wednesday. “Moreover, attackers are quickly altering the nations they’re concentrating on on this marketing campaign.”
The brand new wave of assaults is alleged to have been most lively in Australia, Germany, Poland, Spain, Austria, and Italy, amongst others, with assaults spreading to newer nations like Romania, the Netherlands, and Thailand beginning mid-January.
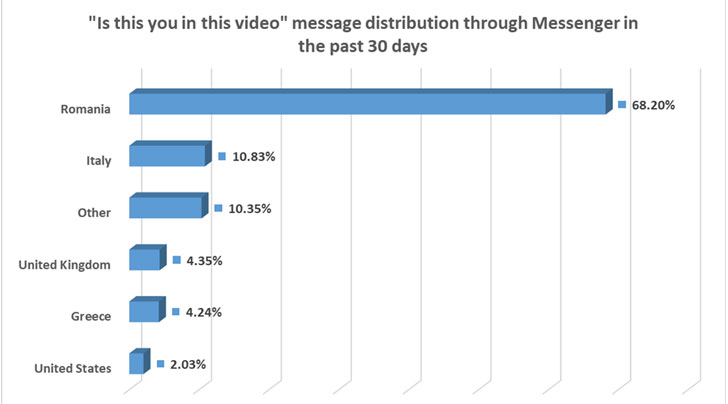
FluBot (aka Cabassous) campaigns use smishing as the first supply methodology to focus on potential victims, whereby customers obtain an SMS message with the query “Is that this you on this video?” and are tricked into clicking a hyperlink that installs the malware.
“This new vector for banking trojans exhibits that attackers want to broaden previous the common malicious SMS messages,” the researchers mentioned.
TeaBot masquerades as QR Code Scanner Apps
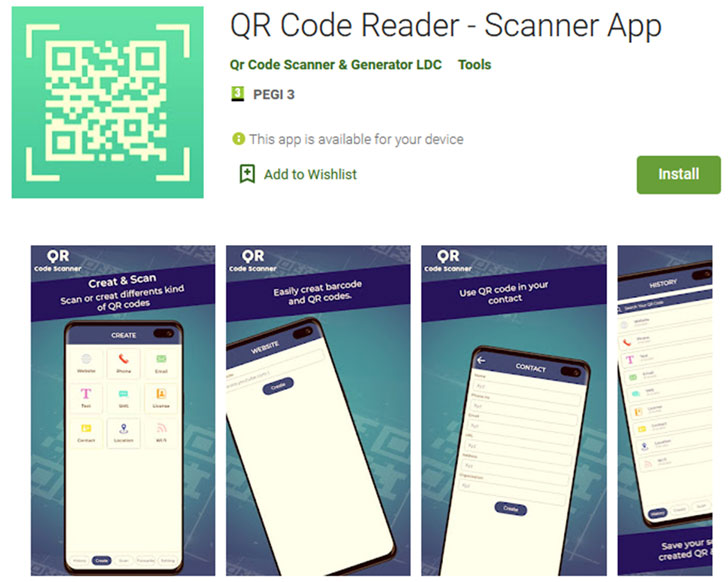
It is not simply FluBot. One other Android trojan known as TeaBot (aka Anatsa) has been noticed lurking on the Google Play Retailer within the type of an app named “QR Code Reader – Scanner App,” attracting no fewer than 100,000 downloads whereas delivering 17 completely different variants of the malware between December 6, 2021, and January 17, 2022.
In a tactic that is turning into more and more frequent, the app does provide the promised performance, but it surely’s additionally designed to retrieve a malicious APK file hosted on GitHub, however not earlier than ascertaining that the nation code of the present registered operator would not begin with a “U.”
The set up of the rogue app then includes presenting a faux UI notifying the person that an add-on replace is required and that the setting to permit installs from unknown sources must be enabled in an effort to apply the replace.
BitDefender mentioned it recognized 4 extra dropper apps — 2FA Authenticator, QR Scanner APK, QR Code Scan, and Sensible Cleaner — that had been out there on the Play Retailer and distributed the TeaBot malware since at the least April 2021.
One other strategy of curiosity adopted by the operators is versioning, which works by submitting a benign model of an app to the app retailer for functions of evading the assessment course of put in place by Google, solely to exchange the codebase over time with further malicious performance via updates at a later date.
Past circumventing the Play Retailer protections to succeed in a wider an infection pool, the malware authors are believed to have paid to seem in Google Adverts served inside different professional purposes and video games, “giving them display time in an app that would have hundreds of thousands of customers.”
The evaluation additionally corroborates a earlier report from Dutch cybersecurity agency ThreatFabric, which discovered six Anatsa droppers on the Play Retailer since June 2021. The apps had been programmed to obtain an “replace” adopted by prompting customers to grant them Accessibility Service privileges and permissions to put in apps from unknown third-party sources.
In a associated improvement, researchers from Pradeo discovered {that a} two-factor authenticator app known as “2FA Authenticator” distributed via the Google Play retailer and downloaded greater than 10,000 occasions was saddled with a banking trojan named Vultr, which targets monetary providers to steal customers’ banking info.
“The applying known as 2FA Authenticator is a dropper leveraged to unfold malware on its customers’ gadgets,” the researchers mentioned. “It has been developed to look professional and supply an actual service. To take action, its builders used the open-source code of the official Aegis authentication software to which they injected malicious code.”
“Malicious actors deal with malware like a product, with improvement and versioning, working onerous to bypass safety applied sciences and achieve extra victims,” Richard Melick, director of product technique for endpoint safety at Zimperium, mentioned.
“When one model will get disrupted, the malicious actors return to growing the subsequent model, particularly when the outcomes have been efficient. And the cellular endpoint is an extremely profitable goal for attackers,” Melick added.
From GriftHorse to Darkish Herring
The event comes as Zimperium zLabs disclosed particulars of one more premium service abuse marketing campaign alongside the strains of GriftHorse that leveraged as many as 470 innocuous-looking apps to subscribe customers to paid providers costing $15 per 30 days with out their information.
The billing fraud, additionally categorized as “fleeceware,” is alleged to have affected upwards of 105 million customers throughout greater than 70 nations, with most victims positioned in Egypt, Finland, India, Pakistan, and Sweden.
The mammoth operation, which the cellular safety firm codenamed “Darkish Herring,” has been backtraced to March 2020, making it one of many longest-running cellular SMS scams found to this point.
Whereas the massive nest of trojan apps have since been purged from the Play Retailer, they’re nonetheless out there on third-party app shops, as soon as once more underscoring the potential risks in relation to sideloading purposes onto cellular gadgets.
“Along with over 470 Android purposes, the distribution of the purposes was extraordinarily well-planned, spreading their apps throughout a number of, assorted classes, widening the vary of potential victims,” Zimperium researcher Aazim Yaswant mentioned. “The apps themselves additionally functioned as marketed, rising the false sense of confidence.”
[ad_2]