[ad_1]
Researchers have demonstrated a brand new kind of fingerprinting approach that exploits a machine’s graphics processing unit (GPU) as a method to trace customers throughout the net persistently.
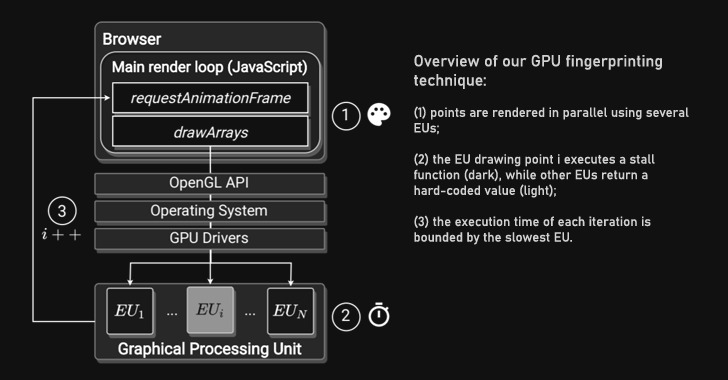
Dubbed DrawnApart, the tactic “identifies a tool from the distinctive properties of its GPU stack,” researchers from Australia, France, and Israel stated in a brand new paper,” including ” variations in velocity among the many a number of execution items that comprise a GPU can function a dependable and strong machine signature, which will be collected utilizing unprivileged JavaScript.”
A tool fingerprint or machine fingerprint is data that’s collected in regards to the {hardware}, put in software program, in addition to the net browser and its related add-ons from a distant computing machine for the aim of distinctive identification.
Fingerprints could be a double-edged sword. On the one hand, a fingerprint algorithm could permit a service supplier (e.g., financial institution) to detect and forestall identification theft and bank card fraud. However it can be abused to compile long-term information of people’ shopping exercise for focused promoting.
Browser fingerprinting, in the same vein, primarily depends on stitching collectively key items of data gleaned from the browser to create the fingerprint. The attributes run the gamut, spanning the browser’s model, OS, timezone, display, language, record of fonts, and even the way in which the browser renders textual content and graphics.
However browser fingerprints additionally endure from one main disadvantage in that they will evolve over time, making it tougher to trace customers for prolonged intervals. That is the place DrawnApart is available in.
It is not solely the first-of-its-kind mechanism to discover and weaponize the manufacturing variations between an identical GPUs, but in addition for reliably utilizing the strategy to tell apart between machines with an identical {hardware} and software program configurations, successfully undermining customers’ privateness.
At its core, the proposed monitoring system entails measuring the time required to render totally different graphics primitives utilizing the WebGL API, every focusing on totally different execution items that comprise a GPU, to create a fingerprint hint that is then fed right into a deep studying community to uniquely establish the particular machine that generated it.
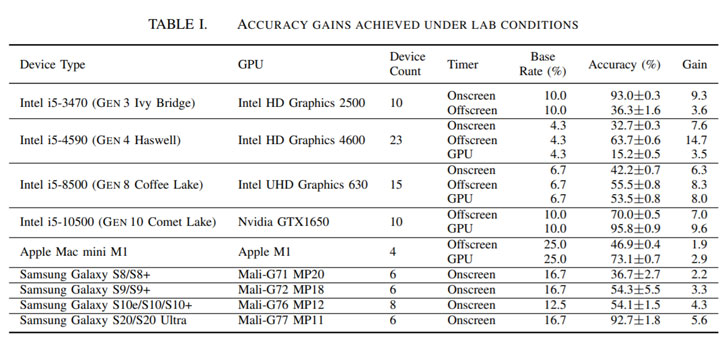
In an analysis setup constituting 88 gadgets, together with Home windows 10 desktops, Apple Mac mini gadgets, and a number of generations of Samsung Galaxy smartphones, the researchers discovered that when used along side state-of-the-art fingerprint linking algorithms like FP-STALKER, DrawnApart prolonged the median common monitoring interval from 17.5 days to twenty-eight days.
Countermeasures to dam the GPU fingerprinting technique vary from script blocking to disabling WebGL, and limiting every net web page to a single execution unit, and even turning off hardware-accelerated rendering — a transfer the researchers warn might severely have an effect on usability and responsiveness.
Moreover, the continued growth into the WebGPU normal — at present accessible in canary releases of Google Chrome and Mozilla Firefox — is predicted to drastically cut back the time taken to gather the fingerprint, prompting the lecturers to conclude that the “results of accelerated compute APIs on consumer privateness must be thought-about earlier than they’re enabled globally.”
[ad_2]