BlackCat ransomware | AT&T Alien Labs
This weblog was collectively written with Santiago Cortes.
Govt abstract
AT&T Alien Labs™ is penning this report about not too long ago created ransomware malware dubbed BlackCat which was utilized in a January 2022 marketing campaign in opposition to two worldwide oil firms headquartered in Germany, Oiltanking and Mabanaft. The assault had little influence on finish clients, however it does serve to remind the cybersecurity group of the potential for risk actors to proceed assaults in opposition to vital infrastructure globally.
Key takeaways:
- The ransomware BlackCat is coded in Rust and was created in November 2021.
- Following tendencies noticed final 12 months by Alien Labs, the ransomware targets a number of platforms (Home windows and Linux), and it makes use of further code to contaminate VMware’s ESXi hypervisor.
- Blackcat makes use of a “wall of disgrace” web site to each blackmail victims, show, and promote their newest campaigns publicly.
- Campaigns stay energetic, with 16 identified incidents in February 2022 as of the publishing of this report.
Background
The 2021 ransomware assault on US-based Colonial Pipeline, which impacted the gasoline provide on the East Coast of America for a number of days, raised consciousness of the truth that adversaries are nicely ready to launch future cyberattacks globally that might severely influence a rustic’s infrastructure. Now, with confrontations within the Ukrainian area taking over new ranges of urgency, there may be heightened expectation of future risk actor campaigns in opposition to the vital infrastructure of western nations. The campaigns might take the type of ransomware assaults or information wiper assaults, as these have been the extremely profitable lately, particularly when mixed with provide chain assaults.
Evaluation
German newspaper Handelsblatt acknowledged the oil firms Oiltanking and Mabanaft had been affected by a ransomware assault on January 29, 2022, that impacted one of many key oil suppliers within the space. The assaults allegedly prompted Shell to re-route their provides so as to keep away from extreme impacts to the German gasoline provide. Even with these actions, it’s been acknowledged that 233 gasoline stations throughout Germany have been affected by the incident, leading to these stations having to run some processes manually and solely taking money fee.
The malware behind these assaults is named BlackCat ransomware, aka ALPHV, as reported by the identical newspaper. The group operates with a ransomware-as-a-service (RaaS) enterprise mannequin, the place the ransomware authors are entitled to 10-20% of the ransom fee, whereas the remainder is stored by the associates deploying the payload. After a profitable assault, victims who refuse to pay the ransom have their particulars posted on darkish internet boards to make assaults public, rising their notoriety and shaming the affected organizations. In line with these blogs, at the least 10 firms could have been impacted by these ransomware campaigns within the first two weeks of February.
Because the malware household operates as a RaaS, the preliminary entry vector depends upon the affiliate occasion deploying the payload and may range from one attacker to a different. Nevertheless, all of them seem to try to exfiltrate victims’ information earlier than beginning the encryption course of, gaining extortion energy for subsequent requests.
The BlackCat gang first appeared in mid-November 2021, and its payload is written within the Rust programming language, which is taken into account to have an identical efficiency to C/C++, however with higher reminiscence administration to keep away from reminiscence errors and concurrent programming. Moreover, it’s a cross platform language, permitting builders to focus on a number of working techniques with the identical code. For these causes, it has been voted because the “most cherished programming language” in Stack Overflow since 2016.
Other than the growing benefits Rust provides, the attackers additionally benefit from a decrease detection ratio from static evaluation instruments, which aren’t normally tailored to all programming languages. For this identical cause, Go Language had grow to be extra well-liked amongst malware coders throughout final 12 months, as seen in different blogs launched by Alien Labs, together with:
Rust has been current in malware samples for a few years, however BlackCat is the primary professionally/commercialized distributed malware household utilizing it, and probably the most affluent so far.
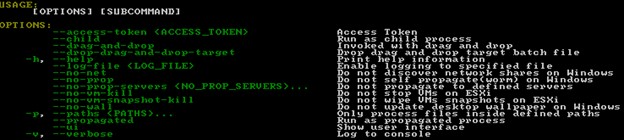
When executed, the malware provides a number of choices for customizing its execution. These choices have advanced since its first model, proven in determine 2 which compares one of many first samples out there (reported by MalwareHunterTeain December 2021) to the newest samples/variations.
Determine 1. @malwrhunterteam screenshot of execution.
Most arguments are non-compulsory, however access-token is enforced to bypass the dynamic evaluation carried out by automated sandboxes. Nevertheless, any token offered bypasses the restriction and permits malware execution. This token, along with the host universally distinctive identifier (UUID), is later used to establish the sufferer in a Tor web site hosted by the attackers, which shows the worth for the information decryptor.
Amongst these choices, Alien Labs has noticed how a few of them are particular to VMware ESXi. This inclusion follows tendencies noticed in 2021 amongst different well-liked RaaS teams, like DarkSide or REvil, who added Linux capabilities to incorporate VMware ESXi of their scope of potential targets. The hypervisor ESXi permits a number of digital machines (VM) to share the identical onerous drive storage. Nevertheless, this additionally permits attackers to encrypt the centralized digital onerous drives used to retailer information from throughout VMs, doubtlessly inflicting disruptions to firms.
The BlackCat malware has code similar to its predecessors. It first goals to cease any operating VMs in ESXi. By doing this, the attacker ensures no different VM is dealing with the information to be encrypted, avoiding corruption problems with the encrypted information. Moreover, any ESXi snapshots are eliminated to harden restoration from the assault.
Extra preparation procedures are carried out by the BlackCat malware on Home windows techniques. For instance, it carries out some noisy actions that may be detected with Alien Labs correlation guidelines, as seen in Appendix A:
- Delete Quantity Shadow Copies Companies to harden restoration from the assault. The command used is ‘vssadmin.exe Delete Shadows /all /quiet’.
- Disables the restoration mode in BCDedit: ‘bcdedit.exe /set {default} recoveryenabled No’.
- Maximize the worth of community requests the Server Service can take by altering the worth within the registry to 65535. This alteration eludes points accessing too many information directly throughout the encryption course of. The command used is: ‘reg add HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesLanmanServerParameters /v MaxMpxCt /d 65535 /t REG_DWORD /f ’.
- If enabled, it makes an attempt to propagate with psexec into totally different techniques. The command runs from the %TEMP% folder, leveraging the credentials within the config file and the mum or dad’s execution choices for propagation choices. ‘psexec.exe -accepteula {Goal} -u {consumer} -p {password} -s -d -f -c {payload}.exe {inherited execution flags}’.
- Clears all of the occasion logs with wevtutil with the command: ‘cmd.exe /c for /F “tokens=*” %1 in (‘wevtutil.exe el’) DO wevtutil.exe cl “%1″’.
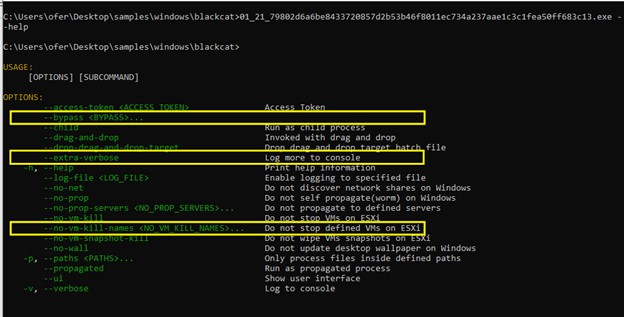
Along with the choices proven in determine 1, the newest samples have added three further features that enhance the ransomware capabilities. These modifications preserve the road of labor already seen, with out together with any main modifications to the way in which the malware operates.
Determine 2. Newest pattern executed.
The present default configuration file appended with the newest noticed executable, consists of amongst others:
- The general public key
- The file extension to make use of for encrypted information, which corresponds to seven alphanumeric characters (0hzoagy for one of many newest samples)
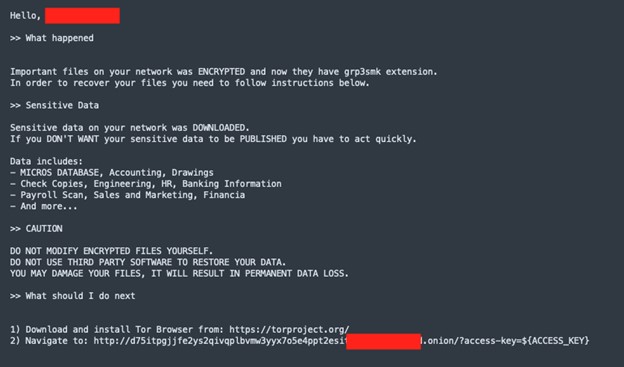
- A ransom word (see determine 3) incorporates the sufferer’s identify a number of instances in addition to the kind of information BlackCat has exfiltrated
- An inventory of pre-obtained credentials from the sufferer which might be for use throughout execution
- An inventory of companies the sufferer ought to kill based on the attacker, earlier than executing the encryption course of — normally companies modifying information that might corrupt information or backup companies that might grow to be counter-productive to the malicious execution. The checklist consists of: mepocs, memtas, veeam, svc$, backup, sql, vss, msexchange, sql$, mysql, mysql$, sophos, MSExchange, MSExchange$, WSBExchange, PDVFSService, BackupExecVSSProvider, BackupExecAgentAccelerator, BackupExecAgentBrowser, BackupExecDiveciMediaService, BackupExecJobEngine, BackupExecManagementService, BackupExecRPCService, GxBlr, GxVss, GxClMgrS, GxCVD, GxCIMgr, GXMMM, GxVssHWProv, GxFWD, SAPService, SAP, SAP$, SAPD$, SAPHostControl, SAPHostExec, QBCFMonitorService, QBDBMgrN, QBIDPService, AcronisAgent, VeeamNFSSvc, VeeamDeploymentService, VeeamTransportSvc, MVArmor, MVarmor64, VSNAPVSS, AcrSch2Svc.
Determine 3. Instance of ransom word.
- An inventory of processes to be killed earlier than executing the encryption course of, with an identical goal because the companies checklist: agntsvc, dbeng50, dbsnmp, encsvc, excel, firefox, infopath, isqlplussvc, msaccess, mspub, mydesktopqos, mydesktopservice, notepad, ocautoupds, ocomm, ocssd, onenote, oracle, outlook, powerpnt, sqbcoreservice, sql, steam, synctime, tbirdconfig, thebat, thunderbird, visio, winword, wordpad, xfssvccon, *sql*, bedbh, vxmon, benetns, bengien, pvlsvr, beserver, raw_agent_svc, vsnapvss, CagService, QBIDPService, QBDBMgrN, QBCFMonitorService, SAP, TeamViewer_Service, TeamViewer, tv_w32, tv_x64, CVMountd, cvd, cvfwd, CVODS, saphostexec, saposcol, sapstartsrv, avagent, avscc, DellSystemDetect, EnterpriseClient, VeeamNFSSvc, VeeamTransportSvc, VeeamDeploymentSvc.
- An inventory of excluded directories, filenames and file extensions to make sure the pc is operative after the encryption.
- Directories: system quantity data, intel, $home windows.~ws, software information, $recycle.bin, mozilla, $home windows.~bt, public, msocache, home windows, default, all customers, tor browser, programdata, boot, config.msi, google, perflogs, appdata, home windows.previous.
- Filenames: desktop.ini, autorun.inf, ntldr, bootsect.bak, thumbs.db, boot.ini, ntuser.dat, iconcache.db, bootfont.bin, ntuser.ini, ntuser.dat.log.
- File extensions: themepack, nls, diagpkg, msi, lnk, exe, cab, scr, bat, drv, rtp, msp, prf, msc, ico, key, ocx, diagcab, diagcfg, pdb, wpx, hlp, icns, rom, dll, msstyles, mod, ps1, ics, hta, bin, cmd, ani, 386, lock, cur, idx, sys, com, deskthemepack, shs ,ldf, theme, mpa, nomedia, spl, cpl, adv, icl, msu.
The ransom word then factors to a Tor onion area with the sector ‘access-key=’ to establish the sufferer and present the worth to recuperate their information with the Decrypt App. Costs are indicated in Bitcoin and Monero, the newest has a reduction over Bitcoin.
Really helpful actions
- Preserve software program with the newest safety updates.
- Monitor and strongly, repeatedly talk to staff to not open and report suspicious emails.
- Use a backup system to backup server information.
- Set up Antivirus and/or endpoint detection and response on all endpoints.
- Be certain that two-factor authentication is enabled in all companies.
Conclusion
Latest ransomware assaults carried out on German oil suppliers had been profitable, however they didn’t have a big influence on the nation’s infrastructure. Nevertheless, contemplating geo-political occasions in Jap Europe, these assaults ought to function a robust reminder that organizations should stay on excessive alert in opposition to cyberattacks. They need to study current campaigns corresponding to these run with BlackCat malware to coach groups and preserve up-to-date detections for the newest risk actor ways, methods, and procedures (TTPs). Like most assaults and risk actor campaigns, BlackCat ransomware can obtain Preliminary Entry utilizing many alternative variations which might be depending on the affiliate working the assault. Nevertheless, the payload might be very related for infections. Blue groups can use this technical data to enhance their readiness in opposition to the newest RaaS assaults.
Alien Labs will proceed to watch variations of BlackCat malware and can replace any actions on the Alien Labs Open Risk Trade™, which is a free, international open risk intelligence group with greater than 200,000 customers publishing up to date risk intelligence day by day. We ship this data within the type of “pulses” that may be shared publicly and privately. As well as, members of OTX can obtain thousands and thousands of indicators of compromise (IOCs), together with these related to BlackCat via integration with the platform.
Alien Labs is monitoring IOCs related to the geo-political battle in Jap Europe, via tagged pulses that monitor incident and associated risk intelligence. To get probably the most up to date data be part of OTX and go to this URL to see the total checklist of pulses related to potential campaigns which may be associated to the Ukranian/Russian battle and risk actors concentrating on different nations.
Appendix A. Detection strategies
The next related detection strategies are in use by Alien Labs. They can be utilized by readers to tune or deploy detections in their very own environments or for aiding further analysis.
|
USM Wherever Correlation Guidelines |
|
Eliminated all snapshots utilizing vimcmd |
|
Home windows Shadow Copies Deletion |
|
Home windows PSExec Utilization |
|
Home windows PSExec Service Utilization |
|
Home windows SMB Server Most Concurrent Requests Set To Most Worth |
|
Home windows Occasion Log Eliminated with wevtutil |
|
Suspicious Bcdedit Utilization |
|
YARA RULES |
rule BlackCat : WindowsMalware {
meta:
writer = "AlienLabs"
description = "Detects BlackCat payloads."
SHA256 = "6660d0e87a142ab1bde4521d9c6f5e148490b05a57c71122e28280b35452e896"
strings:
$rust = "/rust/" ascii broad
$a0 = "vssadmin.exe Delete Shadows /all /quietshadow" ascii
$a1 = "bcdedit /set {default}bcdedit /set {default} recoveryenabled No" ascii broad
$a2 = "CompaniesLanmanServerParameters /v MaxMpxCt /d 65535" ascii broad
$a3 = ".onion/?access-key=${ACCESS_KEY}" ascii broad
$b0 = "config_id" ascii
$b1 = "public_key" ascii
$b2 = "extension" ascii
$b3 = "note_file_name" ascii
$b4 = "enable_esxi_vm_kill" ascii
$b5 = "enable_esxi_vm_snapshot_kill" ascii
situation:
uint16(0) == 0x5A4D and filesize < 5MB and $rust and a couple of of ($a*) and three of ($b*)
}
|
rule LinuxBlackCat : LinuxMalware {
meta:
writer = "AlienLabs"
description = "Detects BlackCat payloads."
SHA256 = "5121f08cf8614a65d7a86c2f462c0694c132e2877a7f54ab7fcefd7ee5235a42"
strings:
$rust = "/rust/" ascii broad
$a0 = "esxcli vm course of kill --type=power --world-id=" ascii broad
$a1 = ".onion/?access-key=${ACCESS_KEY}" ascii broad
$b0 = "config_id" ascii
$b1 = "public_key" ascii
$b2 = "extension" ascii
$b3 = "note_file_name" ascii
$b4 = "enable_esxi_vm_kill" ascii
$b5 = "enable_esxi_vm_snapshot_kill" ascii
situation:
uint32(0) == 0x464c457f and filesize < 5MB and $rust and all of ($a*) and three of ($b*)
}
|
Appendix B. Related indicators (IOCs)
The next technical indicators are related to the reported intelligence. An inventory of indicators can also be out there within the OTX Pulse. Please word, the heart beat could embrace different actions associated however out of the scope of the report.
|
TYPE |
INDICATOR |
DESCRIPTION |
|
SHA256 |
f2b3f1ed693021b20f456a058b86b08abfc4876c7a3ae18aea6e95567fd55b2e |
Home windows BlackCat Payload |
|
SHA256 |
cefea76dfdbb48cfe1a3db2c8df34e898e29bec9b2c13e79ef40655c637833ae |
Home windows BlackCat Payload |
|
SHA256 |
7e363b5f1ba373782261713fa99e8bbc35ddda97e48799c4eb28f17989da8d8e |
Home windows BlackCat Payload |
|
SHA256 |
f837f1cd60e9941aa60f7be50a8f2aaaac380f560db8ee001408f35c1b7a97cb |
Home windows BlackCat Payload |
|
SHA256 |
731adcf2d7fb61a8335e23dbee2436249e5d5753977ec465754c6b699e9bf161 |
Home windows BlackCat Payload |
|
SHA256 |
7b2449bb8be1b37a9d580c2592a67a759a3116fe640041d0f36dc93ca3db4487 |
Home windows BlackCat Payload |
|
SHA256 |
38834b796ed025563774167716a477e9217d45e47def20facb027325f2a790d1 |
Home windows BlackCat Payload |
|
SHA256 |
40f57275721bd74cc59c0c59c9f98c8e0d1742b7ae86a46e83e985cc4039c3a5 |
Home windows BlackCat Payload |
|
SHA256 |
b588823eb5c65f36d067d496881d9c704d3ba57100c273656a56a43215f35442 |
Home windows BlackCat Payload |
|
SHA256 |
f815f5d6c85bcbc1ec071dd39532a20f5ce910989552d980d1d4346f57b75f89 |
Home windows BlackCat Payload |
|
SHA256 |
0c6f444c6940a3688ffc6f8b9d5774c032e3551ebbccb64e4280ae7fc1fac479 |
Home windows BlackCat Payload |
|
SHA256 |
c5ad3534e1c939661b71f56144d19ff36e9ea365fdb47e4f8e2d267c39376486 |
Home windows BlackCat Payload |
|
SHA256 |
7154fdb1ef9044da59fcfdbdd1ed9abc1a594cacb41a0aeddb5cd9fdaeea5ea8 |
Home windows BlackCat Payload |
|
SHA256 |
658e07739ad0137bceb910a351ce3fe4913f6fcc3f63e6ff2eb726e45f29e582 |
Home windows BlackCat Payload |
|
SHA256 |
5bdc0fb5cfbd42de726aacc40eddca034b5fa4afcc88ddfb40a3d9ae18672898 |
Home windows BlackCat Payload |
|
SHA256 |
c8b3b67ea4d7625f8b37ba59eed5c9406b3ef04b7a19b97e5dd5dab1bd59f283 |
Home windows BlackCat Payload |
|
SHA256 |
bd337d4e83ab1c2cacb43e4569f977d188f1bb7c7a077026304bf186d49d4117 |
Home windows BlackCat Payload |
|
SHA256 |
28d7e6fe31dc00f82cb032ba29aad6429837ba5efb83c2ce4d31d565896e1169 |
Home windows BlackCat Payload |
|
SHA256 |
15b57c1b68cd6ce3c161042e0f3be9f32d78151fe95461eedc59a79fc222c7ed |
Home windows BlackCat Payload |
|
SHA256 |
4e18f9293a6a72d5d42dad179b532407f45663098f959ea552ae43dbb9725cbf |
Home windows BlackCat Payload |
|
SHA256 |
13828b390d5f58b002e808c2c4f02fdd920e236cc8015480fa33b6c1a9300e31 |
Home windows BlackCat Payload |
|
SHA256 |
c3e5d4e62ae4eca2bfca22f8f3c8cbec12757f78107e91e85404611548e06e40 |
Home windows BlackCat Payload |
|
SHA256 |
1af1ca666e48afc933e2eda0ae1d6e88ebd23d27c54fd1d882161fd8c70b678e |
Home windows BlackCat Payload |
|
SHA256 |
3d7cf20ca6476e14e0a026f9bdd8ff1f26995cdc5854c3adb41a6135ef11ba83 |
Home windows BlackCat Payload |
|
SHA256 |
722f1c1527b2c788746fec4dd1af70b0c703644336909735f8f23f6ef265784b |
Home windows BlackCat Payload |
|
SHA256 |
d767524e1bbb8d50129485ffa667eb1d379c745c30d4588672636998c20f857f |
Home windows BlackCat Payload |
|
SHA256 |
aae77d41eba652683f3ae114fadec279d5759052d2d774f149f3055bf40c4c14 |
Home windows BlackCat Payload |
|
SHA256 |
be8c5d07ab6e39db28c40db20a32f47a97b7ec9f26c9003f9101a154a5a98486 |
Home windows BlackCat Payload |
|
SHA256 |
9f6876762614e407d0ee6005f165dd4bbd12cb21986abc4a3a5c7dc6271fcdc3 |
Home windows BlackCat Payload |
|
SHA256 |
79802d6a6be8433720857d2b53b46f8011ec734a237aae1c3c1fea50ff683c13 |
Home windows BlackCat Payload |
|
SHA256 |
2cf54942e8cf0ef6296deaa7975618dadff0c32535295d3f0d5f577552229ffc |
Home windows BlackCat Payload |
|
SHA256 |
bacedbb23254934b736a9daf6de52620c9250a49686d519ceaf0a8d25da0a97f |
Home windows BlackCat Payload |
|
SHA256 |
3c8ad2dae0b1bb536925b4e8d5a87e77c6134371eada2c7628358d6c6d3083dc |
Home windows BlackCat Payload |
|
SHA256 |
67d1f4077e929385cfd869bf279892bf10a2c8f0af4119e4bc15a2add9461fec |
Home windows BlackCat Payload |
|
SHA256 |
5a604a8f0e72f3bf7901b7b67f881031a402ab8072269c00233a554df548f54d |
Home windows BlackCat Payload |
|
SHA256 |
6660d0e87a142ab1bde4521d9c6f5e148490b05a57c71122e28280b35452e896 |
Home windows BlackCat Payload |
|
SHA256 |
f8c08d00ff6e8c6adb1a93cd133b19302d0b651afd73ccb54e3b6ac6c60d99c6 |
Linux BlackCat Payload |
|
SHA256 |
5121f08cf8614a65d7a86c2f462c0694c132e2877a7f54ab7fcefd7ee5235a42 |
Linux BlackCat Payload |
|
SHA256 |
3a08e3bfec2db5dbece359ac9662e65361a8625a0122e68b56cd5ef3aedf8ce1 |
Linux BlackCat Payload |
|
SHA256 |
f7a038f9b91c40e9d67f4168997d7d8c12c2d27cd9e36c413dd021796a24e083 |
Linux BlackCat Payload |
|
SHA256 |
9802a1e8fb425ac3a7c0a7fca5a17cfcb7f3f5f0962deb29e3982f0bece95e26 |
Linux BlackCat Payload |
Appendix C. Mapped to MITRE ATT&CK
The findings of this report are mapped to the next MITRE ATT&CK Matrix methods:
- TA0005: Protection Evasion
- T1070: Indicator Removing on Host
- T1070.001: Clear Home windows Occasion Logs
- T1078: Legitimate Accounts
- T1078.003: Native Accounts
- T1562: Impair Defenses
- T1562.001: Disable or Modify Instruments
- T1070: Indicator Removing on Host
- TA0010: Exfiltration
- T1048: Exfiltration Over Different Protocol
- T1048.002: Exfiltration Over Uneven Encrypted Non-C2 Protocol
- T1048: Exfiltration Over Different Protocol
- TA0040: Influence
- T1486: Knowledge Encrypted for Influence
Appendix D. Reporting context
The next checklist of sources was utilized by the report writer(s) throughout the assortment and evaluation course of related to this intelligence report.
- https://www.varonis.com/weblog/alphv-blackcat-ransomware
- https://unit42.paloaltonetworks.com/blackcat-ransomware
Alien Labs charges sources primarily based on the Intelligence supply and knowledge reliability score system to evaluate the reliability of the supply and the assessed stage of confidence we place on the knowledge distributed. The next chart incorporates the vary of potentialities, and the choice utilized to this report..
Supply reliability A1
|
RATING |
DESCRIPTION |
|
A – Dependable |
Little doubt concerning the supply’s authenticity, trustworthiness, or competency. Historical past of full reliability. |
|
B – Normally Dependable |
Minor doubts. Historical past of principally legitimate data. |
|
C – Pretty Dependable |
Doubts. Offered legitimate data previously. |
|
D – Not Normally Dependable |
Vital doubts. Offered legitimate data previously. |
|
E – Unreliable |
Lacks authenticity, trustworthiness, and competency. Historical past of invalid data. |
|
F – Reliability Unknown |
Inadequate data to judge reliability. Could or is probably not dependable. |
Data reliability A2
|
RATING |
DESCRIPTION |
|
1 – Confirmed |
Logical, per different related data, confirmed by unbiased sources. |
|
2 – In all probability True |
Logical, per different related data, not confirmed. |
|
3 – Probably True |
Fairly logical, agrees with some related data, not confirmed. |
|
4 – Doubtfully True |
Not logical however doable, no different data on the topic, not confirmed. |
|
5 – Inconceivable |
Not logical, contradicted by different related data. |
|
6 – Can’t be judged |
The validity of the knowledge cannot be decided. |
Suggestions
AT&T Alien Labs welcomes suggestions concerning the reported intelligence and supply course of. Please contact the Alien Labs report writer or contact labs@alienvault.com.