Consultants Discover Some Associates of BlackMatter Now Spreading BlackCat Ransomware
An evaluation of two ransomware assaults has recognized overlaps within the ways, strategies, and procedures (TTPs) between BlackCat and BlackMatter, indicating a robust connection between the 2 teams.
Whereas it is typical of ransomware teams to rebrand their operations in response to elevated visibility into their assaults, BlackCat (aka Alphv) marks a brand new frontier in that the cyber crime cartel is constructed out of associates of different ransomware-as-a-service (RaaS) operations.
BlackCat first emerged in November 2021 and has since focused a number of organizations worldwide over the previous few months. It has been known as out for being much like BlackMatter, a short-lived ransomware household that originated from DarkSide, which attracted notoriety for its high-profile assault on Colonial Pipeline in Might 2021.
In an interview with Recorded Future’s The File final month, a BlackCat consultant dismissed rumors that it is a rebranding of BlackMatter, whereas noting that it is made up of associates related to different RaaS teams.
“Partly, we’re all linked to gandrevil [GandCrab / REvil], blackside [BlackMatter / DarkSide], mazegreggor [Maze / Egregor], lockbit, and so forth., as a result of we’re adverts (aka associates),” the unnamed consultant was quoted as saying. “We borrowed their benefits and eradicated their disadvantages.”
“BlackCat appears to be a case of vertical enterprise growth,” Cisco Talos researchers Tiago Pereira and Caitlin Huey mentioned. “In essence, it is a technique to management the upstream provide chain by making a service that’s key to their enterprise (the RaaS operator) higher suited to their wants and including one other income.”
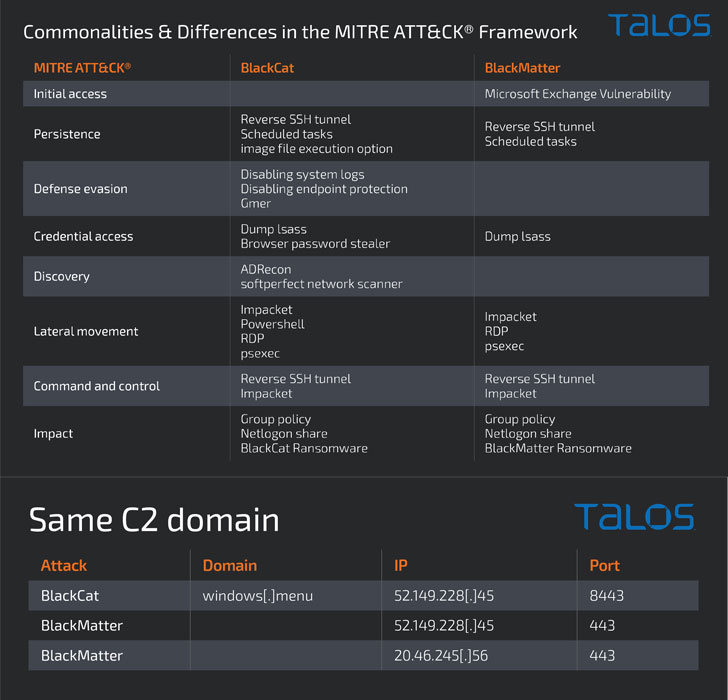
What’s extra, the cybersecurity agency mentioned it noticed plenty of commonalities between a BlackMatter assault in September 2021 and that of a BlackCat assault from December 2021, together with the instruments and the file names used in addition to a site employed to keep up persistent entry to the goal community.
This overlapping use of the identical command-and-control deal with has raised the chance that the affiliate that used BlackMatter was probably one of many early adopters of BlackCat, with each the assaults taking greater than 15 days to succeed in the encryption stage.
“As we’ve got seen a number of instances earlier than, RaaS companies come and go. Their associates, nonetheless, are more likely to merely transfer on to a brand new service. And with them, most of the TTPs are more likely to persist,” the researchers mentioned.
The findings come as BlackBerry detailed a brand new .NET-based ransomware household known as LokiLocker that not solely encrypts the information but in addition incorporates an non-obligatory wiper performance that is designed to erase all non-system information and overwrite the grasp boot document (MBR) ought to a sufferer refuse to pay up inside a specified timeframe.
“LokiLocker works as a limited-access ransomware-as-a-service scheme that seems to be bought to a comparatively small variety of fastidiously vetted associates behind closed doorways,” the researchers mentioned. Lively since not less than August 2021, a majority of victims detected thus far are concentrated in Japanese Europe and Asia.