Hackers Exploiting Contaminated Android Gadgets to Register Disposable Accounts
An evaluation of SMS phone-verified account (PVA) companies has led to the invention of a rogue platform constructed atop a botnet involving hundreds of contaminated Android telephones, as soon as once more underscoring the failings with counting on SMS for account validation.
SMS PVA companies, since gaining prevalence in 2018, present customers with different cellular numbers that can be utilized to register for different on-line companies and platforms, and assist bypass SMS-based authentication and single sign-on (SSO) mechanisms put in place to confirm new accounts.
“Such a service can be utilized by malicious actors to register disposable accounts in bulk or create phone-verified accounts for conducting fraud and different felony actions,” Development Micro researchers stated in a report printed final week.
Telemetry knowledge gathered by the corporate exhibits that a lot of the infections are situated in Indonesia (47,357), adopted by Russia (16,157), Thailand (11,196), India (8,109), and France (5,548), Peru (4,915), Morocco (4,822), South Africa (4,413), Ukraine (2,920), and Malaysia (2,779).
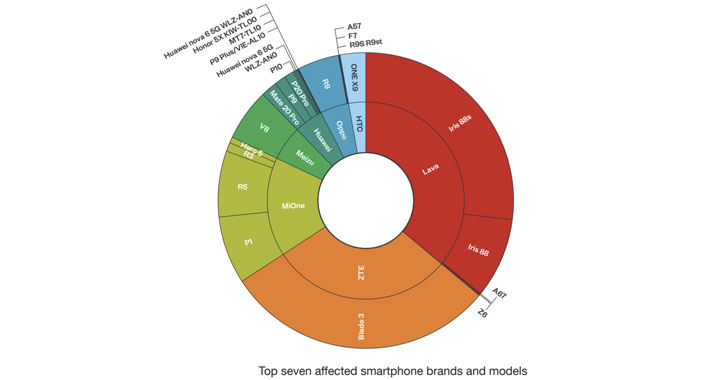
A majority of affected gadgets are price range Android telephones assembled by unique tools producers resembling Lava, ZTE, Mione, Meizu, Huawei, Oppo, and HTC.
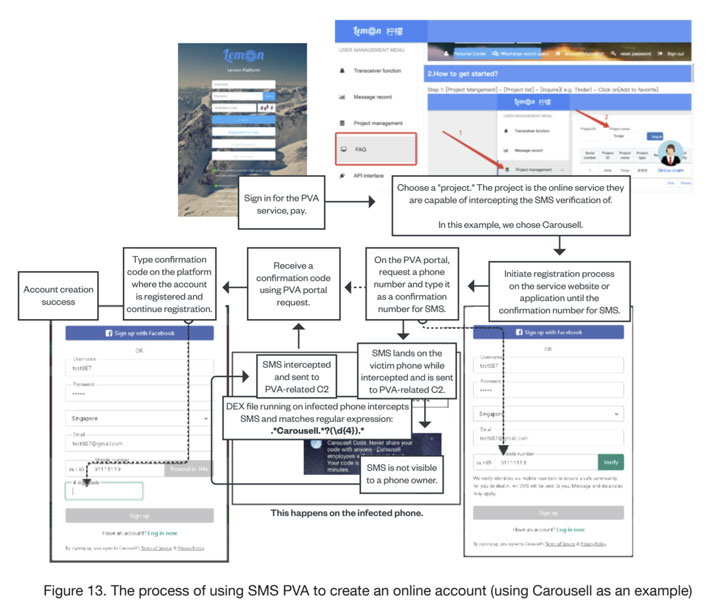
One specific service, dubbed smspva[.]web, contains of Android telephones contaminated with SMS-intercepting malware, which the researchers suspect might have occurred in both of two methods: via malware downloaded unintentionally by the customers or via malicious software program preloaded into the gadgets throughout manufacturing, implying a supply-chain compromise.
The underground VPA service advertises “bulk digital cellphone numbers” to be used on varied platforms by way of an API, along with claiming to be in possession of cellphone numbers spanning throughout greater than 100 international locations.
The Guerrilla malware (“plug.dex“), for its half, is engineered to parse SMS messages obtained on the affected Android cellphone, verify them in opposition to particular search patterns obtained from a distant server, after which exfiltrate the messages that match these expressions again to the server.
“The malware stays low-profile, amassing solely the textual content messages that match the requested software in order that it may well covertly proceed this exercise for lengthy durations,” the researchers stated. “If the SMS PVA service permits its prospects to entry all messages on the contaminated telephones, the house owners would rapidly discover the issue.”
With on-line portals usually authenticating new accounts by cross-checking the placement (i.e., IP tackle) of the customers in opposition to their cellphone numbers throughout registration, SMS PVA companies get round this restriction by making use of residential proxies and VPNs to connect with the specified platform.
What’s extra, these companies solely promote the one-time affirmation codes wanted on the time of account registration, with the botnet operator utilizing the military of compromised gadgets to obtain, look at, and report the SMS verification codes with out the house owners’ information and consent.
In different phrases, the botnet facilitates quick access to hundreds of cellular numbers in numerous international locations, successfully enabling the actors to register new accounts en masse and use them for varied scams and even take part in coordinated inauthentic consumer habits.
“The presence of SMS PVA companies makes one other dent on the integrity of SMS verification as the first technique of account validation,” the researchers stated.
“The size to which SMS PVA is ready to provide cellular numbers implies that the standard strategies to make sure validity — resembling blocklisting cellular numbers beforehand tied to account abuse or figuring out numbers belonging to VoIP companies or SMS gateways — will not be sufficient.”