
‘Inventive’ Facial Verification with Generative Adversarial Networks
A brand new paper from Stanford College has proposed a nascent technique for fooling facial authentication programs in platforms similar to relationship apps, by utilizing a Generative Adversarial Community (GAN) to create different face photographs that include the identical important ID data as an actual face.
The tactic efficiently bypassed facial verification processes on relationship functions Tinder and Bumble, in a single case even passing off a gender-swapped (male) face as genuine to the supply (feminine) identification.

Varied generated identities which function the precise encoding of the paper’s creator (featured in first picture above). Supply: https://arxiv.org/pdf/2203.15068.pdf
In keeping with the creator, the work represents the primary try to bypass facial verification with using generated photographs which have been imbued with particular identification traits, however which try to characterize an alternate or considerably altered identification.
The method was examined on a customized native face verification system, after which carried out properly in black field assessments in opposition to two relationship functions that carry out facial verification on user-uploaded photographs.
The brand new paper is titled Face Verification Bypass, and comes from Sanjana Sarda, a researcher on the Division of Electrical Engineering at Stanford College.
Controlling the Face House
Although ‘injecting’ ID-specific options (i.e. from faces, highway indicators, and so on.) into crafted photographs is a staple of adversarial assaults, the brand new examine suggests one thing totally different: that the analysis sector’s rising capacity to management the latent area of GANs will ultimately allow the event of architectures that may create constant different identities to that of a person – and, successfully, allow the extraction of identification options from web-available photographs of an unsuspecting person to coopt right into a ‘shadow’ crafted identification.
Consistency and navigability have been the first challenges concerning the latent area of the GAN ever for the reason that inception of Generative Adversarial Networks. A GAN that has efficiently assimilated a group of coaching photographs into its latent area gives no simple map to ‘push’ options from one class to a different.
Whereas methods and instruments similar to Gradient-weighted Class Activation Mapping (Grad-CAM) will help to ascertain latent instructions between the established lessons, and allow transformations (see picture beneath), the additional problem of entanglement normally makes for an ‘approximative’ journey, with restricted wonderful management of the transition.
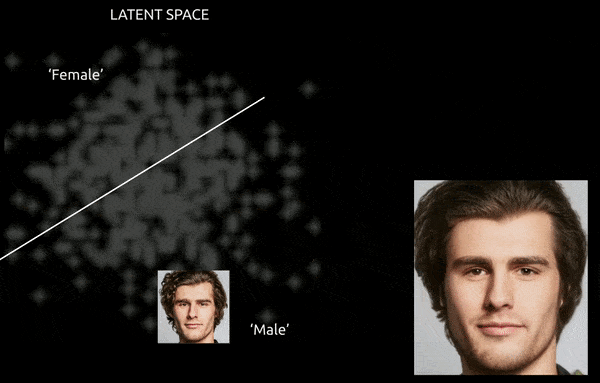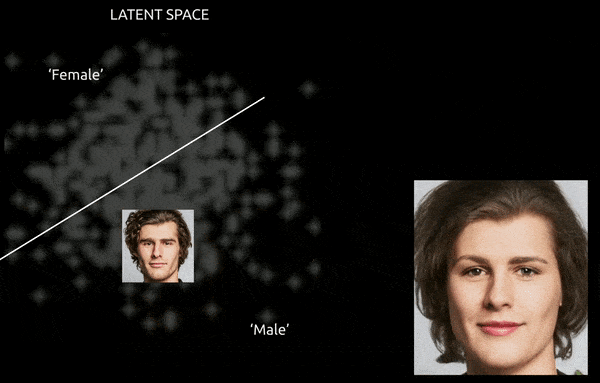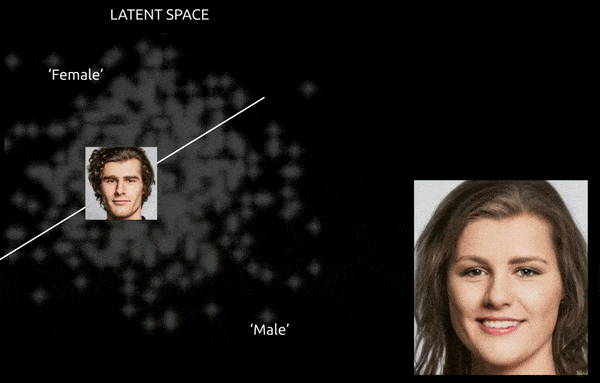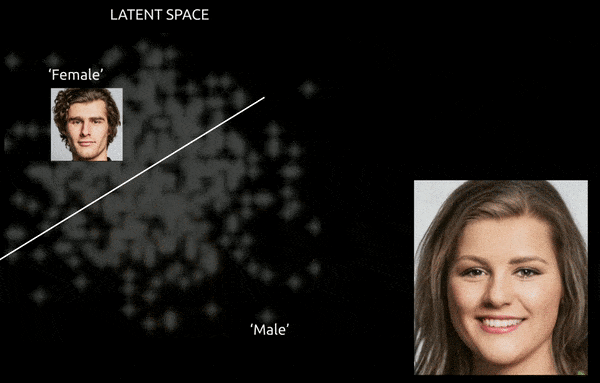
A tough journey between encoded vectors in a GAN’s latent area, pushing a data-derived male identification into the ‘feminine’ encodings on the opposite aspect of considered one of many linear hyperplanes within the complicated and arcane latent area. Picture derived from materials at https://www.youtube.com/watch?v=dCKbRCUyop8
The flexibility to ‘freeze’ and defend ID-specific options whereas shifting them into transformative encodings elsewhere within the latent area doubtlessly makes it attainable to create a constant (and even animatable) particular person whose identification is learn by machine programs as another person.
Methodology
The creator used two datasets as the idea for experiments: a Human Consumer Dataset consisting of 310 photographs of her face spanning a interval of 4 years, with various lighting, age, and examine angles), with cropped faces extracted by way of Caffe; and the racially balanced 108,501 photographs within the FairFace dataset, equally extracted and cropped.
The native facial verification mannequin was derived from a base implementation of FaceNet and DeepFace, pre-trained on ConvNet Inception, with every picture represented by a 128-dimensional vector.
The strategy makes use of face photographs from a educated subset from FairFace. With the intention to cross facial verification, the calculated distance brought on by a picture’s Frobenius norm is offset in opposition to the goal person within the database. Any picture underneath the brink of 0.7 equates to the identical identification, else verification is taken into account to have failed.
A StyleGAN mannequin was fine-tuned on the creator’s private dataset, producing a mannequin that might generate recognizable variations of her identification, although none of those generated photographs have been equivalent to the coaching knowledge. This was achieved by freezing the primary 4 layers within the discriminator, to keep away from overfitting of the info and produce variegated output.
Although various photographs have been obtained with the bottom StyleGAN mannequin, the low decision and constancy prompted a second try with StarGAN V2, which permits the coaching of seed photographs in direction of a goal face.
The StarGAN V2 mannequin was pre-trained over roughly 10 hours utilizing the FairFace validation set, on a batch measurement of 4 and a validation measurement of 8. In probably the most profitable strategy, the creator’s private dataset was used because the supply with coaching knowledge as a reference.
Verification Experiments
A facial verification mannequin was constructed primarily based on a subset of 1000 photographs, with the intention of verifying an arbitrary picture from the set. Photos that handed verification efficiently have been subsequently examined in opposition to the creator’s personal ID.

On the left, the paper’s creator, an actual photograph; center, an arbitrary picture that failed verification; proper, an unrelated picture from the dataset that handed verification because the creator.
The target of the experiments was to create as huge a spot as attainable between the perceived visible identification whereas retaining the defining traits of the goal identification. This was evaluated with Mahalanobis distance, a metric utilized in picture processing for sample and template search.
For the baseline generative mannequin, the low-resolution outcomes obtained show restricted variety, regardless of passing native facial verification. StarGAN V2 proved extra able to creating various photographs that have been in a position to authenticate.

All photographs depicted handed native facial verification. Above are the low-resolution StyleGAN baseline generations, beneath, the higher-res and better high quality StarGAN V2 generations.
The ultimate three photographs illustrated above used the creator’s personal face dataset as each supply and reference, whereas the previous photographs used coaching knowledge as reference and the creator’s dataset as supply.
The ensuing generated photographs have been examined in opposition to the facial verification programs of relationship apps Bumble and Tinder, with the creator’s identification because the baseline, and handed verification. A ‘male’ era of the creator’s face additionally handed Bumble’s verification course of, although the lighting needed to be adjusted within the generated picture earlier than it was accepted. Tinder didn’t settle for the male model.

‘Maled’ variations of the creator’s (feminine) identification.
Conclusion
These are seminal experiments in identification projection, within the context of GAN latent area manipulation, which stays a unprecedented problem in picture synthesis and deepfake analysis. Nonetheless, work opens up the idea of embedding extremely particular options constantly throughout various identities, and of making ‘alternate’ identities that ‘learn’ as another person.
First revealed thirtieth March 2022.














