New iLOBleed Rootkit Concentrating on HP Enterprise Servers with Knowledge Wiping Assaults
A beforehand unknown rootkit has been discovered setting its sights on Hewlett-Packard Enterprise’s Built-in Lights-Out (iLO) server administration know-how to hold out in-the-wild assaults that tamper with the firmware modules and fully wipe knowledge off the contaminated techniques.
The invention, which is the primary occasion of real-world malware in iLO firmware, was documented by Iranian cybersecurity agency Amnpardaz this week.
“There are quite a few elements of iLO that make it a perfect utopia for malware and APT teams: Extraordinarily excessive privileges (above any stage of entry within the working system), very low-level entry to the {hardware}, being completely out of the sight of the admins, and safety instruments, the overall lack of awareness and instruments for inspecting iLO and/or defending it, the persistence it offers for the malware to stay even after altering the working system, and particularly being at all times operating and by no means shutting down,” the researchers stated.
In addition to managing the servers, the truth that iLO modules have broad entry to all of the firmware, {hardware}, software program, and working system (OS) put in on the servers make them a perfect candidate to breach organizations utilizing HP servers, whereas additionally enabling the malware to take care of persistence after reboots and survive OS reinstallations. Nevertheless, the precise modus operandi used to infiltrate the community infrastructure and deploy the wiper stays unknown as but.
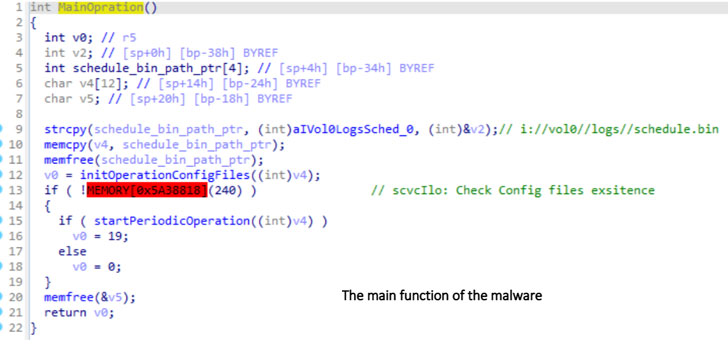
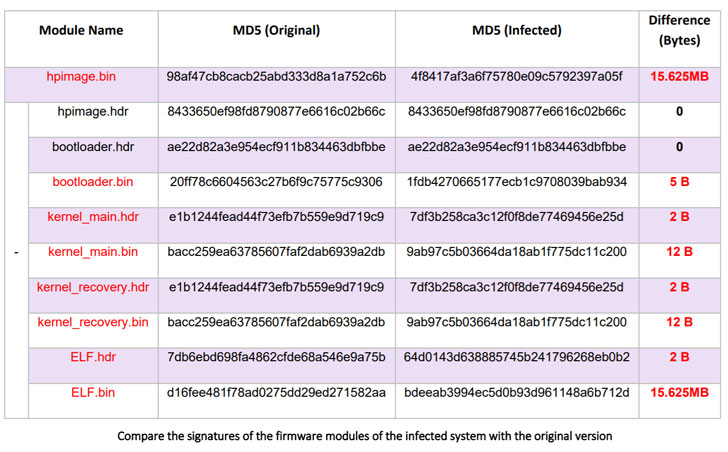
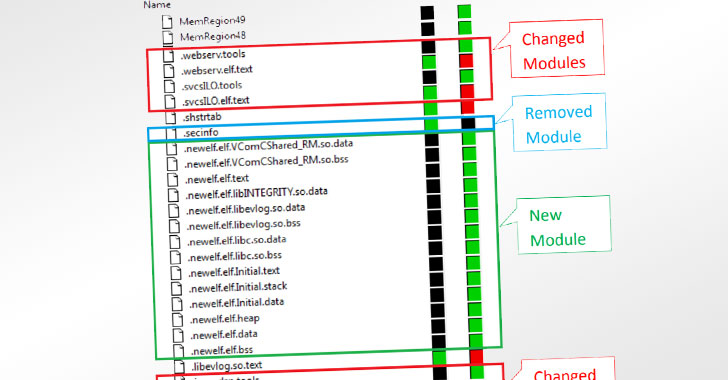
Dubbed iLOBleed, the rootkit has been put to make use of in assaults since 2020 with the objective of manipulating numerous unique firmware modules as a way to stealthily impede updates to the firmware. Particularly, the modifications made to the firmware routine simulates the firmware improve course of — by purportedly displaying the precise firmware model and including related logs — when in actuality no updates are carried out.
“This alone reveals that the aim of this malware is to be a rootkit with most stealth and to cover from all safety inspections,” the researchers stated. “A malware that, by hiding in some of the highly effective processing assets (which is at all times on), is ready to execute any instructions obtained from an attacker, with out ever being detected.”
Though the adversary stays unidentified, Amnpardaz described the rootkit as possible the work of a sophisticated persistent risk (APT), a designation a nation-state or state-sponsored group that employs steady, clandestine, and complicated hacking methods to realize unauthorized entry to a system and stay inside for a protracted time period with out attracting consideration.
If something, the event as soon as once more brings firmware safety into sharp focus, necessitating that firmware updates shipped by the producer are promptly utilized to mitigate potential dangers, iLO networks are segmented from the working networks, and that the firmware is periodically monitored for indicators of an infection.
“One other vital level is that there are strategies to entry and infect iLO each via the community and thru the host working system,” the researchers famous. “Which means that even when the iLO community cable is totally disconnected, there’s nonetheless the opportunity of an infection with the malware. Apparently, there isn’t a approach to flip off or disable iLO fully in case it isn’t wanted.”