North Korean Hackers Utilizing Home windows Replace Service to Infect PCs with Malware
The infamous Lazarus Group actor has been noticed mounting a brand new marketing campaign that makes use of the Home windows Replace service to execute its malicious payload, increasing the arsenal of living-off-the-land (LotL) methods leveraged by the APT group to additional its aims.
The Lazarus Group, also called APT38, Hidden Cobra, Whois Hacking Group, and Zinc, is the moniker assigned to the North Korea-based nation-state hacking group that is been energetic since not less than 2009. Final yr, the risk actor was linked to an elaborate social engineering marketing campaign concentrating on safety researchers.
The most recent spear-phishing assaults, which Malwarebytes detected on January 18, originate from weaponized paperwork with job-themed lures impersonating the American international safety and aerospace firm Lockheed Martin.
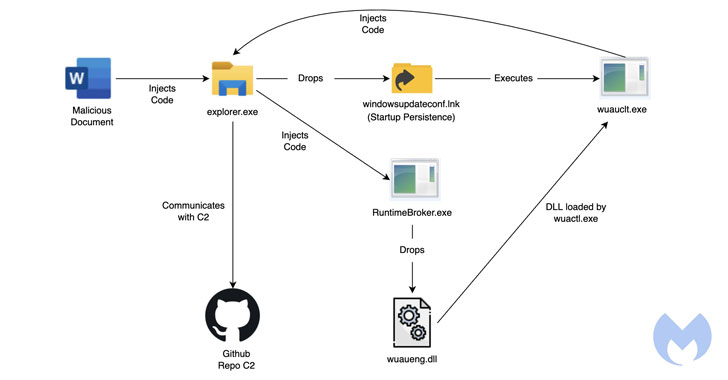
Opening the decoy Microsoft Phrase file triggers the execution of a malicious macro embedded inside the doc that, in flip, executes a Base64-decoded shellcode to inject a lot of malware elements into the explorer.exe course of.
Within the subsequent section, one of many loaded binaries, “drops_lnk.dll,” leverages the Home windows Replace shopper to run a second module known as “wuaueng.dll.” “That is an attention-grabbing approach utilized by Lazarus to run its malicious DLL utilizing the Home windows Replace Shopper to bypass safety detection mechanisms,” researchers Ankur Saini and Hossein Jazi famous.
The cybersecurity agency characterised “wuaueng.dll” as “some of the essential DLLs within the assault chain,” whose fundamental function is to determine communications with a command-and-control (C2) server – a GitHub repository internet hosting malicious modules masquerading as PNG picture information. The GitHub account is alleged to have been created on January 17, 2022.
Malwarebytes mentioned that the hyperlinks to Lazarus Group are based mostly on a number of items of proof tying them to previous assaults by the identical actor, together with infrastructure overlaps, doc metadata, and the usage of job alternatives template to single out its victims.
“Lazarus APT is likely one of the superior APT teams that’s identified to goal the protection business,” the researchers concluded. “The group retains updating its toolset to evade safety mechanisms. Despite the fact that they’ve used their outdated job theme technique, they employed a number of new methods to bypass detections.”
















