Vital Bugs in Management Net Panel Expose Linux Servers to RCE Assaults
Researchers have disclosed particulars of two important safety vulnerabilities in Management Net Panel that could possibly be abused as a part of an exploit chain to attain pre-authenticated distant code execution on affected servers.
Tracked as CVE-2021-45467, the difficulty considerations a case of a file inclusion vulnerability, which happens when an online software is tricked into exposing or working arbitrary information on the net server.
Management Net Panel, beforehand CentOS Net Panel, is an open-source Linux management panel software program used for deploying hosting environments.
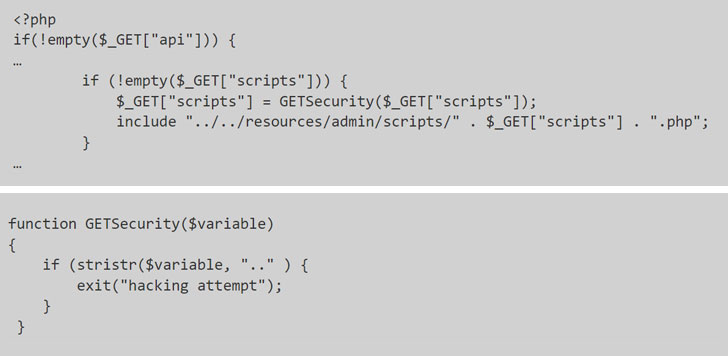
Particularly, the difficulty arises when two of the unauthenticated PHP pages used within the software — “/consumer/login.php” and “/consumer/index.php” — fail to adequately validate a path to a script file, in response to Octagon Networks’ Paulos Yibelo, who found and reported the issues.
Which means so as to exploit the vulnerability, all an attacker has to do is to change the embody assertion, which is used to incorporate the content material of 1 PHP file into one other PHP file, to inject malicious code from a distant useful resource and obtain code execution.
Apparently, whereas the appliance had protections in place to flag efforts to change to a father or mother listing (denoted by “..”) as a “hacking try” it did nothing to forestall the PHP interpreter from accepting a specifically crafted string comparable to “.$00.” and successfully reaching a full bypass.
This not solely permits a foul actor to entry restricted API endpoints, it may be used along with an arbitrary file write vulnerability (CVE-2021-45466) to realize full distant code execution on the server as follows —
- Ship a null byte powered file inclusion payload so as to add malicious API key
- Use API key to put in writing to a file (CVE-2021-45466)
- Use step #1 to incorporate the file we simply wrote into (CVE-2021-45467)
Following accountable disclosure, the issues have since been addressed by the CWP maintainers together with updates shipped earlier this month.